Definition and Purpose of DD Form 254
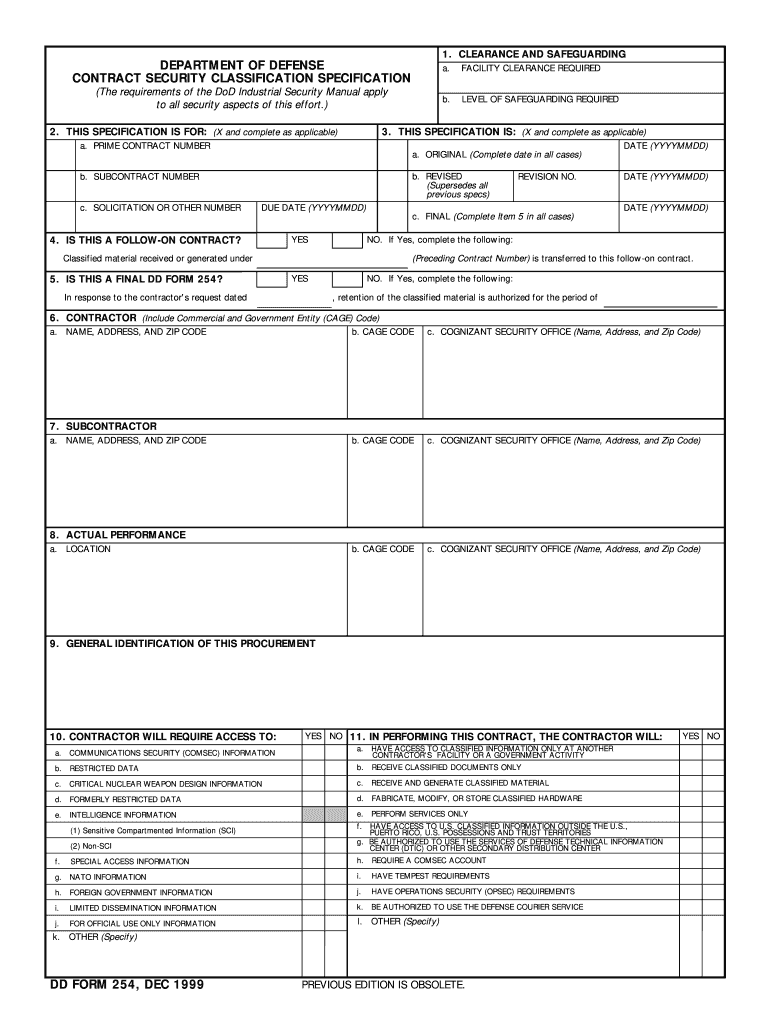
DD Form 254, also known as the Department of Defense Contract Security Classification Specification, serves as an official document detailing the security requirements for contractors working with classified materials for the Department of Defense (DoD). The form outlines how information should be safeguarded based on the assigned classification levels. It is essential for contractors to understand the specific security measures required to protect sensitive information to comply with federal regulations and ensure national security.
It includes comprehensive sections that specify the type of security clearance required, the classification levels of the information involved, and any additional security guidance that contractors must adhere to. This ensures that both the contractor and the government maintain rigorous security standards throughout the duration of a contract.
Key Components of DD Form 254
- Security Classification: The form indicates the classification levels, such as Confidential, Secret, or Top Secret.
- Contractor Information: Contains the contractor’s details, including name, address, and data pertinent to the contract.
- Access Requirements: Describes what information the personnel involved have access to, helping to prevent unauthorized dissemination.
- Restrictions on Information: Outlines any additional security measures or access restrictions specific to the project.
How to Complete DD Form 254
Completing a DD Form 254 involves several steps to ensure that all required information is accurately provided. The following guidelines can help facilitate a smooth completion process.
- Gather Required Information: Collect all necessary details about the contractor, including business name, address, and relevant security clearance levels.
- Identify the Classification Level: Determine the appropriate security classification required for the contract based on the nature of the information being handled.
- Detail Access Requirements: Specify which individuals will need access to classified information and what level of clearance they hold.
- Fill Out Mandatory Sections: Complete all the main sections, ensuring no information is missing that could delay clearance approvals.
- Attach Supporting Documents: If necessary, attach additional documentation that may be required for security clearance.
The accuracy and thoroughness of the completed form are vital, as any errors can lead to delays in processing security clearances.
Importance of Security Measures in DD Form 254
Adherence to the security measures outlined in DD Form 254 is critical for maintaining national security and protecting sensitive information. Contractors must understand the importance of compliance and the ramifications of failing to uphold the standards recorded within the form.
- Protecting Sensitive Information: Unauthorized access to classified materials can jeopardize national security, compromising intelligence and operations.
- Contractor Accountability: Clear guidelines within the form hold contractors accountable for maintaining security protocols and ensuring their employees comply with the necessary classification requirements.
- Legal Compliance: Failure to comply with the requirements outlined in the DD Form 254 can result in legal repercussions, including loss of contract, penalties, or criminal charges.
Common Scenarios for DD Form 254 Use
DD Form 254 is frequently used in various scenarios involving government contracting and classified projects. Below are a few common examples that highlight its application.
- Military Contracting: A defense contractor working on weapon systems requires access to classified specifications to perform their duties.
- Information Technology Projects: Contractors managing cybersecurity for government networks must access sensitive data to protect against potential breaches.
- Research and Development: Firms involved in developing advanced technologies often handle classified information related to national defense initiatives.
In each of these cases, the DD Form 254 is essential for ensuring that only authorized personnel have access to sensitive information, thereby mitigating risks associated with potential security breaches.
Steps to Organize and Manage DD Form 254 Documentation
Proper organization and management of DD Form 254 documentation is key to effective compliance and security management. Here are several steps to ensure that all aspects of the documentation are maintained efficiently.
- Establish a Centralized Record System: Keep all completed DD Forms 254 in a secure cloud-based or physical location for reference and compliance tracking.
- Regular Reviews and Updates: Set a schedule for periodic review of forms to ensure they remain current and aligned with updated security policies or changes in contractor information.
- Training for Personnel: Implement training programs for employees involved in handling classified information to reinforce the importance of compliance with security measures outlined in the DD Form 254.
- Audit Trails: Maintain records of who has accessed the forms and any changes made to provide a clear audit trail for potential evaluations.
By establishing a systematic approach to manage documents associated with DD Form 254, contractors can enhance their compliance and security posture.
Electronic vs. Paper Format of DD Form 254
The DD Form 254 is available in both electronic and paper formats, each with its own set of advantages and considerations.
-
Electronic Format:
- Convenience: The electronic lay-out allows for easier edits and updates.
- Storage: Digital forms require less physical space and can be backed up for protection against loss.
- Collaboration: Multiple users can access and edit forms in real-time, streamlining the process among team members.
-
Paper Format:
- Traditional Use: Many organizations still prefer to use paper forms for formal submissions.
- Signatures: Some may find it more convenient to provide handwritten signatures on physical documents, which may be legally required in certain cases.
Both formats serve the same essential purpose, and choosing between them often depends on the organization’s operating procedures and existing technology resources.