Definition and Meaning of Attachment B
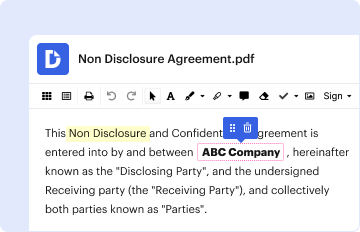
Attachment B is a user security information form utilized within companies to authorize and manage user access rights, primarily for document workflow systems such as DocHub. The form acts as an official record that specifies access permissions for various pipelines, ensuring that only authorized personnel can access sensitive documents. It is crucial for maintaining security compliance and organizational efficiency, reflecting its essential role in corporate environments.
Attachment B is designed as a structured document, typically requiring details such as the company's legal name, user information, and specific access rights. This ensures that each user has the right level of access, reducing the risk of unauthorized data exposure. Companies often rely on Attachment B to set clear boundaries within their digital infrastructures, facilitating controlled access to critical resources.
How to Use Attachment B
Using Attachment B involves a systematic approach to ensure accurate completion and submission. The form should be filled out by an authorized representative who is knowledgeable about the company’s operational requirements and user roles.
-
Identify Users: List all individuals requiring access, including their roles and departments. This step ensures that the form accurately reflects all parties needing document access.
-
Specify Access Rights: Detail the specific access rights each user requires, such as viewing, editing, or uploading capabilities. Customized access permissions help maintain document integrity and security.
-
Review and Approval: Once completed, the form should be reviewed by a managerial or IT security team to ensure alignment with company policies. Approval confirms that the information provided is complete and correct.
-
Submission: The approved form can be submitted online, faxed, or emailed to the relevant department, such as the IT or HR department, depending on company protocol.
Consistently following these steps helps streamline user access management and supports organizational security governance.
Steps to Complete Attachment B
Completing Attachment B properly is critical for ensuring users have appropriate access levels. Follow these detailed steps for a successful submission:
-
Gather Necessary Information: Collect the company’s legal name, address, and relevant user details, including names, titles, and contact information.
-
Determine Access Needs: Consult with departmental managers to determine the specific access each user requires. This might involve viewing, editing, or admin-level capabilities.
-
Fill Out the Form: Carefully enter each required piece of information into the form. Double-check for accuracy, as errors can affect user access or delay processing.
-
Managerial Review: Have a second pair of eyes review the completed form. This is often someone from the IT or security department who can verify that the details align with company standards and security protocols.
-
Obtain Approval: Secure signatures from required approvers, which may include department heads or IT security authorities. Approval certifies that the request is legitimate and justified.
-
Submit: Send the completed form through the designated submission method. Method of submission—online, fax, or email—depends on company preferences and security considerations.
This structured approach to completing Attachment B ensures that user access is assigned accurately and aligns with organizational security requirements.
Key Elements of Attachment B
Understanding and focusing on the key elements of Attachment B facilitate a comprehensive and accurate completion of the form. Key elements typically include:
-
Company Information: The full legal name and registered address of the company. This ensures that the form can be correctly associated with the appropriate business entity.
-
User Details: Information about each authorized user such as name, job title, and department. Accurate user details are crucial for mapping access rights to the correct individual.
-
Access Specification: Details of the specific permissions each user requires, categorized by document type or access capability, such as read-only, edit, or full control.
-
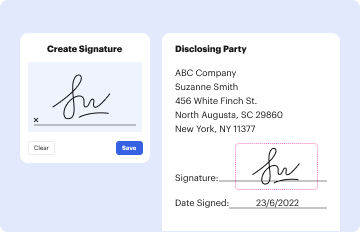
Authorization Signatures: Signatures from authorized individuals, affirming the validity of the form’s information and granting the specified access rights.
-
Submission Information: Instructions for submitting the form, including relevant department contacts and submission methods.
Legal Use of Attachment B
Attachment B serves a pivotal legal role by documenting user access rights to company documents, ensuring compliance with data protection laws such as GDPR and CCPA. Properly executed, the form provides a legal safeguard by proving that the company has taken necessary steps to control and secure document access.
-
Compliance Verification: Attachment B helps demonstrate adherence to legal requirements for data protection and user access control, which can be crucial during audits or legal reviews.
-
Audit Trail: By maintaining records of user access requests and approvals, companies can produce an audit trail when necessary. This record can show how access permissions have been granted and modified over time.
-
Risk Mitigation: The form helps reduce the risk of unauthorized data access by ensuring that only vetted and approved users have the required permissions to sensitive documents.
Form Submission Methods for Attachment B
Different companies may prefer different methods for submitting Attachment B, depending on their infrastructure and security considerations. Common methods include:
-
Online Submission: Via a secure company portal, allowing for quick and efficient processing. Online submission often involves filling out a digital form, which is then automatically routed to the appropriate department for review.
-
Fax: This offers a tangible paper trail, appealing to companies that favor physical copies for record-keeping. Although less commonly used, fax submission can be a secure option if encryption methods are in place.
-
Email: A versatile choice that many companies use, primarily due to its speed and convenience. It is essential to ensure that email submissions are encrypted to protect sensitive information during transmission.
Each method has its pros and cons, and the choice often depends on organizational culture, available technology, and security practices.
Examples of Using Attachment B
There are several practical scenarios where Attachment B proves beneficial:
-
New Employee Onboarding: During onboarding, Attachment B can be filled out to establish initial user access rights for newly hired employees, ensuring they have the necessary tools and permissions to begin their roles.
-
Department Transfers: If an employee is transferred to another department, a new Attachment B can adjust their access rights accordingly to reflect their new responsibilities and reduce security risks.
-
Access Revocation: For employees leaving the organization or changing roles, Attachment B can be updated to revoke or modify access permissions, maintaining strict control over who can access sensitive documents.
In each case, Attachment B serves as a vital tool in document management and security, helping companies safeguard access, maintain compliance, and enhance operational efficiency.