

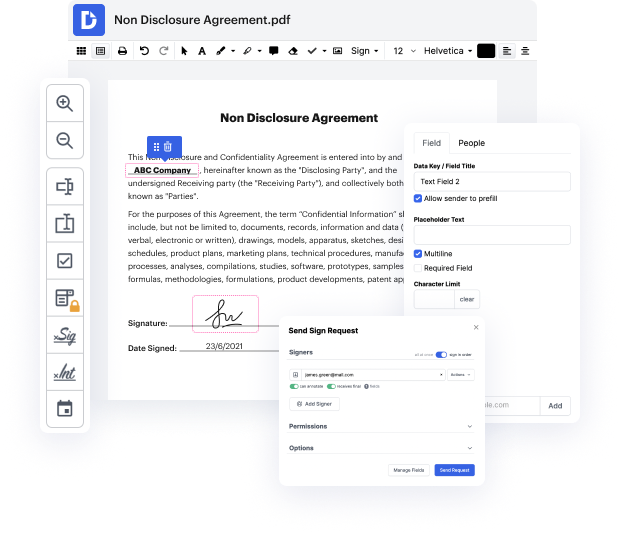
Regardless of how complex and challenging to modify your files are, DocHub delivers a simple way to change them. You can modify any part in your PAP without extra resources. Whether you need to tweak a single component or the whole form, you can entrust this task to our powerful tool for fast and quality outcomes.
In addition, it makes certain that the final file is always ready to use so that you can get on with your projects without any delays. Our all-purpose group of features also comes with sophisticated productivity features and a collection of templates, allowing you to take full advantage of your workflows without the need of wasting time on routine activities. On top of that, you can access your documents from any device and incorporate DocHub with other apps.
DocHub can handle any of your form management activities. With a great deal of features, you can create and export documents however you prefer. Everything you export to DocHub’s editor will be saved securely for as long as you need, with strict protection and data safety frameworks in place.
Check DocHub today and make handling your files easier!
hi and welcome in this video Iamp;#39;ll discuss the three network authentication protocols which operates at layer 2 of the OSI model that is the return link layer now a network authentication protocol basically authenticates the claim of a client once it wants to connect to a network and a good network security design should assume that an attacker can sniff all the network traffic now the first protocol is the parent occation protocol which is a very weak indication protocol because it sends the username and password in clear text so any attacker can sniff the information and can launch a replay attack by replaying these information so this protocol is very weak and should not be used now the next protocol is the challenge handshake authentication protocol or chair now this protocol is more secure because it does not share the password on the network in clear text and passwords are created during the account enrollment process of a client and these passwords are only stored over th