

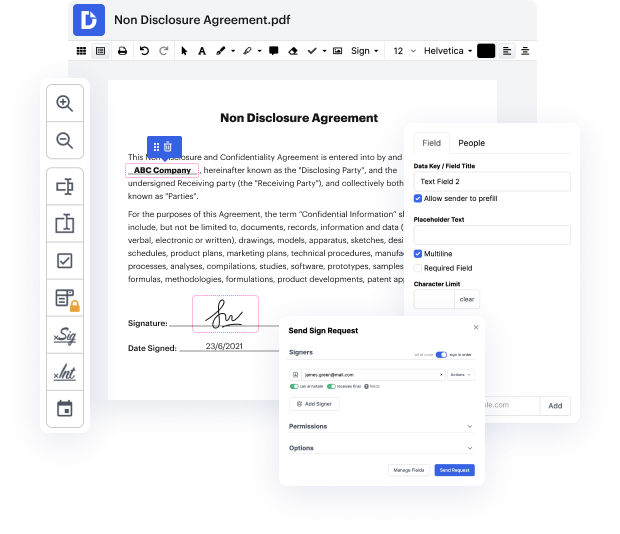
With DocHub, you can easily rework TIN in EZW from any place. Enjoy features like drag and drop fields, editable text, images, and comments. You can collect electronic signatures safely, include an additional level of protection with an Encrypted Folder, and work together with teammates in real-time through your DocHub account. Make adjustments to your EZW files online without downloading, scanning, printing or sending anything.
You can find your edited record in the Documents tab of your account. Create, email, print out, or convert your file into a reusable template. With so many powerful tools, it’s easy to enjoy seamless document editing and management with DocHub.
Anybody remember the riscure embedded hardware CTF a long time ago? Rhme2? I have a whole playlist covering various different challenges. Two of them cover reverse engineering a binary that would be running on the arduino board. Which means their architecture is AVR. And if you are not very familiar with reversing embedded devices or AVR I would recommend watching these videos before continuing here. This video will be about another reversing challenge, but explained by Zeta Two. I didnt solve that challenge, but he was really excited of sharing this write-up with us. This video was planned for a long time and because I still dont have a good process for working with other people I screwed up the first time we recorded this. So thank you for sitting down with me a second time. So Im carl, or on the internet known as zeta two and I play a lot of CTFs. But before we fully head into the technical parts I want to highlight something. I know from the time when all of this stuff was new t