

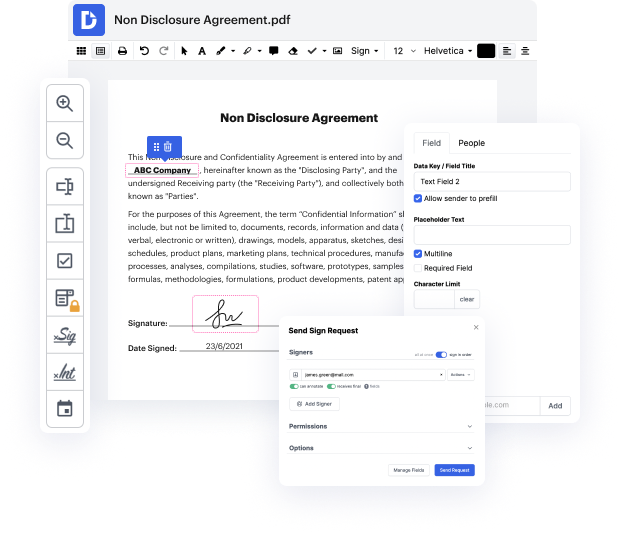
DocHub is an all-in-one PDF editor that allows you to inlay password in DITA, and much more. You can highlight, blackout, or erase paperwork elements, insert text and images where you need them, and collect information and signatures. And because it works on any web browser, you won’t need to update your hardware to access its powerful capabilities, saving you money. When you have DocHub, a web browser is all it takes to manage your DITA.
Sign in to our service and follow these steps:
It couldn't be simpler! Enhance your document processing now with DocHub!
in this video we will be looking at how to extract password information from the ntds.dit file this dip file is the active directory database thereamp;#39;s a copy of it stored on every domain controller and it contains all the account information as well as password secrets from your active directory domain if youamp;#39;re able to compromise this file you can extract all of the password hashes from all the accounts in active directory you do need privileged access to get to this but once you have this file you have access to every account in the domain so letamp;#39;s take a look at how an attacker could compromise this file first if you look at an active directory domain letamp;#39;s see where this file is stored in the windows ntds directory youamp;#39;ll find the ntds.dip file there you may be tempted to just try to copy that file and save it off somewhere if i put in my temp directory here you can see i can try but this file is constantly in use by the active directory servi