

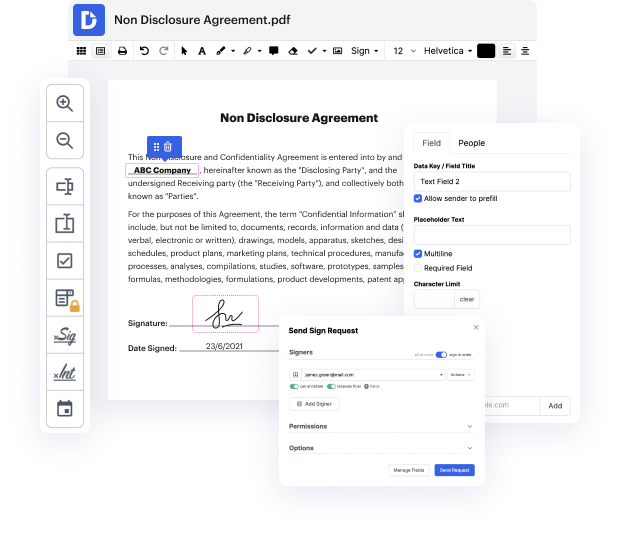
LOG may not always be the easiest with which to work. Even though many editing features are out there, not all give a simple solution. We created DocHub to make editing effortless, no matter the document format. With DocHub, you can quickly and effortlessly inject topic in LOG. In addition to that, DocHub provides an array of additional tools including form creation, automation and management, sector-compliant eSignature solutions, and integrations.
DocHub also helps you save time by creating form templates from documents that you utilize regularly. In addition to that, you can benefit from our a lot of integrations that allow you to connect our editor to your most used programs effortlessly. Such a solution makes it fast and simple to deal with your documents without any slowdowns.
DocHub is a helpful feature for personal and corporate use. Not only does it give a comprehensive set of tools for form generation and editing, and eSignature implementation, but it also has an array of features that come in handy for developing multi-level and straightforward workflows. Anything uploaded to our editor is stored risk-free in accordance with major industry criteria that shield users' information.
Make DocHub your go-to choice and simplify your form-centered workflows effortlessly!
hey everyone this is charles welcome back to the channel in this video weamp;#39;re going to take a look at sql injection sql injection vulnerabilities are one of the most serious and pervasive risks to our web applications as identified by owasp the open web application security project weamp;#39;re going to look at this as it pertains to the certified ethical hacking exam so letamp;#39;s jump in and take a look at an example of how we can do some sql injection testing letamp;#39;s look at injection attacks and we also refer to these as input validation attacks this can include things like sql injection thatamp;#39;s what we most commonly think of when we think of injection attacks weamp;#39;re attempting to insert malicious strings of input maybe into a websiteamp;#39;s login form in hopes that this malicious syntax will give us unexpected control of the web application now although we can certainly use automated tools to attempt this if weamp;#39;re familiar with sql languag