

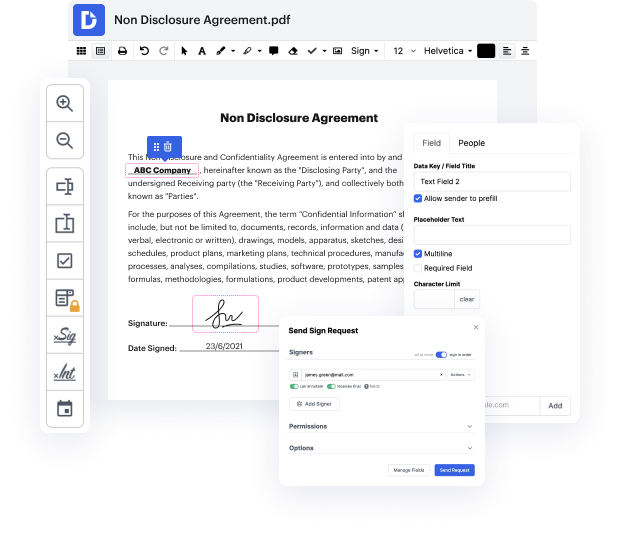
Flaws are present in every tool for editing every document type, and even though you can find a wide variety of tools on the market, not all of them will fit your specific needs. DocHub makes it easier than ever to make and change, and deal with documents - and not just in PDF format.
Every time you need to quickly cut off field in HWPML, DocHub has got you covered. You can quickly alter form components including text and images, and layout. Customize, organize, and encrypt documents, develop eSignature workflows, make fillable documents for smooth information collection, etc. Our templates option enables you to generate templates based on documents with which you frequently work.
In addition, you can stay connected to your go-to productivity features and CRM solutions while dealing with your documents.
One of the most extraordinary things about leveraging DocHub is the ability to handle form tasks of any difficulty, regardless of whether you need a swift modify or more diligent editing. It comes with an all-in-one form editor, website document builder, and workflow-centered features. In addition, you can rest assured that your documents will be legally binding and comply with all security protocols.
Cut some time off your projects with DocHub's capabilities that make handling documents easy.
hey guys in this video Iamp;#39;m going to cover a common active directory credential Harvest technique that Iamp;#39;ve been see fractures use when theyamp;#39;ve compromised and gained access to an organizationamp;#39;s internal Network so obviously gaining creds within a network is going to be high on a for Access objective list as this then allows them to move laterally around a network and then further down the line potentially drop run somewhere to a large amount of devices now theyamp;#39;re obviously multiple ways credentials can potentially be captured however in this video I will cover how an attacker can potentially extract credentials from the Windows registry and thatamp;#39;s done by targeting the Sam and system hive Iamp;#39;m going to preface this video with that this is strictly for educational purposes and is meant to serve a study material for cyber security courses and assist cyber security blue teams and threat Hunters to understand and detect this type of b