

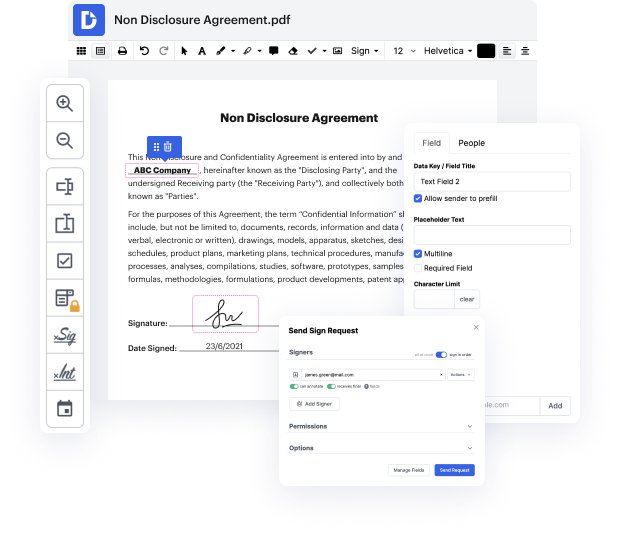
WRF may not always be the best with which to work. Even though many editing features are out there, not all give a simple tool. We developed DocHub to make editing straightforward, no matter the file format. With DocHub, you can quickly and easily wipe out authentication in WRF. In addition to that, DocHub gives a range of other features such as document generation, automation and management, industry-compliant eSignature solutions, and integrations.
DocHub also enables you to save time by producing document templates from documents that you use regularly. In addition to that, you can make the most of our a wide range of integrations that enable you to connect our editor to your most utilized applications with ease. Such a tool makes it quick and easy to work with your files without any slowdowns.
DocHub is a handy tool for individual and corporate use. Not only does it give a all-encompassing suite of tools for document creation and editing, and eSignature integration, but it also has a range of features that come in handy for creating multi-level and straightforward workflows. Anything imported to our editor is kept risk-free according to leading field requirements that safeguard users' data.
Make DocHub your go-to option and simplify your document-based workflows with ease!
what is going on guys itamp;#39;s moded Warfare here and welcome back to another computer tutorial so in this tutorial Iamp;#39;m going to be showing you guys how to bypass different kinds of login systems now this is not done for any malicious purposes the reason is kind of from a developer standpoint to show you guys what is secure and whatamp;#39;s not secure when it comes to creating uh a secure login system so yeah something that I got confused with when I first got into coding and I tried to uh create login systems to protect something and you know Iamp;#39;d watch a video tutorial on how to create a login system Iamp;#39;d create it it would work thatamp;#39;s great and then Iamp;#39;d find out later on that it was completely unsecure and had loads of security Loop poles so thatamp;#39;s the idea behind this video to show you guys how to bypass certain login systems so you know what areas to secure when you make your own login systems or if youamp;#39;re new to coding a