

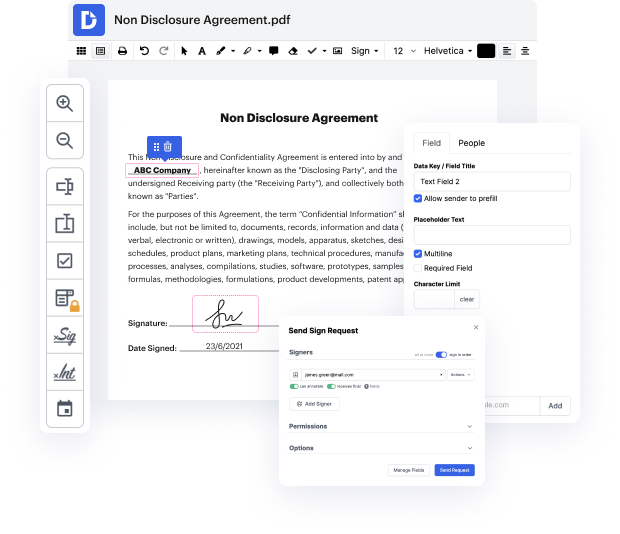
People frequently need to take out PII in text when processing forms. Unfortunately, few applications offer the tools you need to complete this task. To do something like this typically requires switching between multiple software applications, which take time and effort. Luckily, there is a platform that is applicable for almost any job: DocHub.
DocHub is a perfectly-built PDF editor with a full set of valuable features in one place. Editing, signing, and sharing forms is easy with our online solution, which you can use from any online device.
By following these five easy steps, you'll have your revised text quickly. The user-friendly interface makes the process quick and effective - stopping jumping between windows. Start using DocHub today!
Hi - my name is Luke Cartey and Iamp;#39;m a member of the field engineering team here at Semmle. This video is about writing a QL query to find sensitive or personally identifiable information, so called PII, that gets written to log files and application runtime. Today, weamp;#39;ll be looking at a open source e-commerce platform called Shopizer. Itamp;#39; s written in Java and weamp;#39;ll be trying to see whether we can find any of any PII vulnerabilities in Shopizer. Now in order to do that weamp;#39;re going to need to find a way to identify personal identifiable information in the source code. Unfortunately, Shopizer as with many applications doesnamp;#39;t have any sort of semantic markers in the code that tell you what is PII. So what going to do is weamp;#39;re going to start off by writing a heuristic query that selects all fields in the program whose name matches either email percentage credit card percentage or percentage phone percentage. This percentage here is a
At DocHub, your data security is our priority. We follow HIPAA, SOC2, GDPR, and other standards, so you can work on your documents with confidence.
Learn more



