

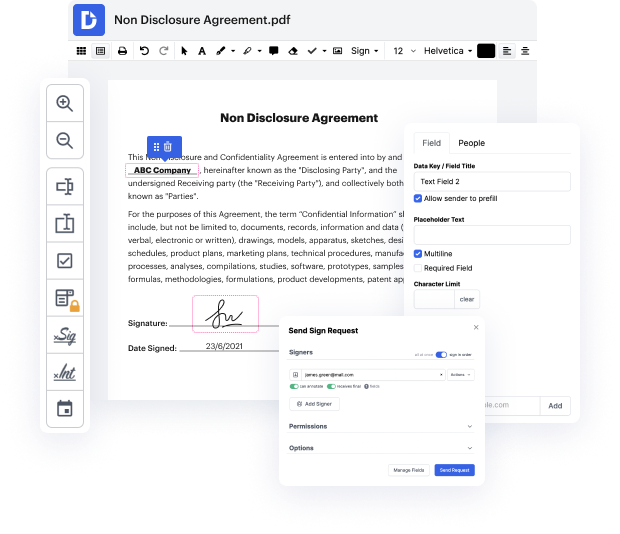
Document generation and approval certainly are a key focus for each company. Whether working with sizeable bulks of documents or a distinct contract, you need to remain at the top of your productiveness. Choosing a excellent online platform that tackles your most frequentl record generation and approval difficulties may result in a lot of work. Numerous online platforms offer only a restricted set of modifying and signature functions, some of which could be valuable to manage ppt file format. A solution that handles any file format and task will be a excellent choice when choosing application.
Get document managing and generation to another level of straightforwardness and excellence without opting for an difficult program interface or costly subscription plan. DocHub provides you with tools and features to deal effectively with all document types, including ppt, and carry out tasks of any difficulty. Edit, organize, and produce reusable fillable forms without effort. Get full freedom and flexibility to strike email in ppt at any moment and securely store all your complete files within your profile or one of many possible incorporated cloud storage space platforms.
DocHub offers loss-free editing, signature collection, and ppt managing on a professional levels. You do not need to go through tiresome guides and invest hours and hours finding out the software. Make top-tier safe document editing a standard process for the everyday workflows.
[MUSIC PLAYING] YUFENG GUO: Hi, and welcome. Were here at the Security Zone at Next with Sam Lugani, an expert in phishing attacks at Google Cloud. SAM LUGANI: Hi, Yufeng. Happy to be here. YUFENG GUO: So phishing attacks are becoming a huge problem today at companies, arent they? SAM LUGANI: Yes, they are. Phishing attacks are a very common type of security attack. In fact, a study conducted by PhishMe showed that 91% of cyberattacks started with a phishing email. YUFENG GUO: Wow. So phishing is one of the main ways that security attackers will attack companies. SAM LUGANI: Yes. Lets walk through an example. [MUSIC PLAYING] Lets say that an attacker is targeting your company and youre the security admin responsible for protecting your organization. So the attacker is going to start by doing some research on your company on LinkedIn, where they can make a list of employees that they want to target. The attacker then sends personalized emails to these employees trying to get them
At DocHub, your data security is our priority. We follow HIPAA, SOC2, GDPR, and other standards, so you can work on your documents with confidence.
Learn more



