

Not all formats, such as ACL, are developed to be easily edited. Even though numerous tools will let us change all document formats, no one has yet created an actual all-size-fits-all solution.
DocHub gives a easy and efficient solution for editing, taking care of, and storing documents in the most widely used formats. You don't have to be a technology-knowledgeable user to shade subject in ACL or make other changes. DocHub is robust enough to make the process straightforward for everyone.
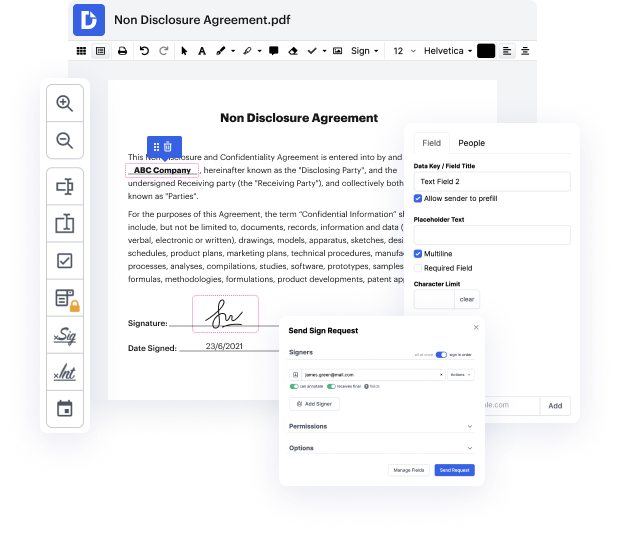
Our tool enables you to change and edit documents, send data back and forth, create dynamic forms for data gathering, encrypt and shield documents, and set up eSignature workflows. Additionally, you can also generate templates from documents you use on a regular basis.
You’ll locate a great deal of other functionality inside DocHub, such as integrations that let you link your ACL document to a variety productivity apps.
DocHub is a straightforward, cost-effective option to handle documents and streamline workflows. It offers a wide selection of features, from generation to editing, eSignature professional services, and web form building. The program can export your paperwork in multiple formats while maintaining highest security and following the maximum data protection criteria.
Give DocHub a go and see just how straightforward your editing process can be.
hello and this is sunny welcome back and Internet is a private network which is heavily protected by many different networking devices such as a router firewall proxy server DMZ honeynet IPs and IDs this diagram is an overly simplified version of the reality I try to pull these devices together in a reasonable order only for teaching and learning purpose today my topic is rotters access control list or ACL a router is used to connect networks together and is primary function is to deliver packets based on layer 3 IP address this is the most important function of a router I will have a separate video talking about the routers today I only focus on one of the routers of security features a CL AC L stands for access control list which is a setup to conquer the traffic in both directions incoming and outgoing a CL tells rodder to permit or deny traffic ing to one or more of the following variables source IP address source subnet mask destination IP address destination subnet mask a