

Disadvantages are present in every solution for editing every file type, and although you can find a lot of tools on the market, not all of them will fit your specific requirements. DocHub makes it easier than ever to make and alter, and handle documents - and not just in PDF format.
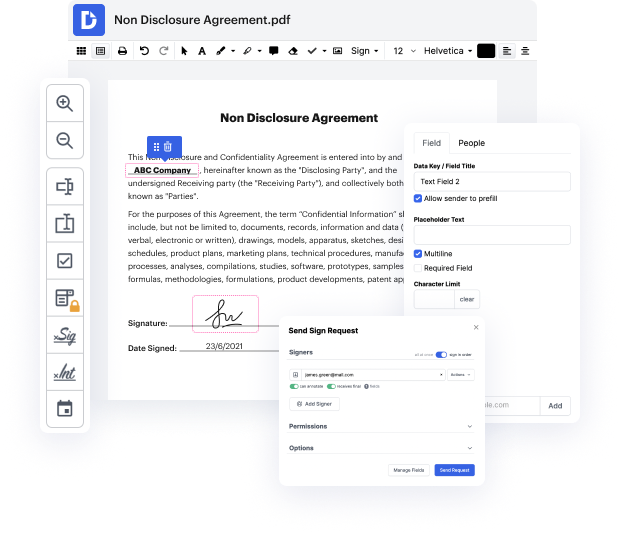
Every time you need to swiftly revise attachment in LOG, DocHub has got you covered. You can easily alter form elements including text and images, and structure. Personalize, arrange, and encrypt files, develop eSignature workflows, make fillable forms for smooth information gathering, and more. Our templates feature enables you to create templates based on documents with which you often work.
In addition, you can stay connected to your go-to productivity features and CRM platforms while handling your files.
One of the most extraordinary things about utilizing DocHub is the option to handle form activities of any difficulty, regardless of whether you require a fast tweak or more diligent editing. It includes an all-in-one form editor, website document builder, and workflow-centered features. In addition, you can be certain that your documents will be legally binding and adhere to all security protocols.
Cut some time off your projects with the help of DocHub's capabilities that make managing files easy.
there are a number of devices that are connected to our networking infrastructure that can provide us with feedback about things that may be occurring on the network these might be switches routers firewalls vpn concentrators and other devices this is a log file from a switch that is giving us information about what interfaces may be going up and down on the switch thereamp;#39;s also security information on the switch the tcp send traffic destined to the local system is automatically blocked for 60 seconds this type of information might vary depending on the logs we are receiving if weamp;#39;re looking at router logs then weamp;#39;d see router updates we may see authentication issues occur with some of these especially if itamp;#39;s a vpn concentrator or things like this tcp syn attack which is related to a network security issue if youamp;#39;ve ever looked at log files on an operating system then you know there is extensive information that you can gather and very often this