


Not all formats, such as 602, are designed to be quickly edited. Even though a lot of tools will let us tweak all form formats, no one has yet created an actual all-size-fits-all tool.
DocHub gives a straightforward and streamlined tool for editing, taking care of, and storing papers in the most widely used formats. You don't have to be a technology-knowledgeable user to replace authentication in 602 or make other modifications. DocHub is powerful enough to make the process easy for everyone.
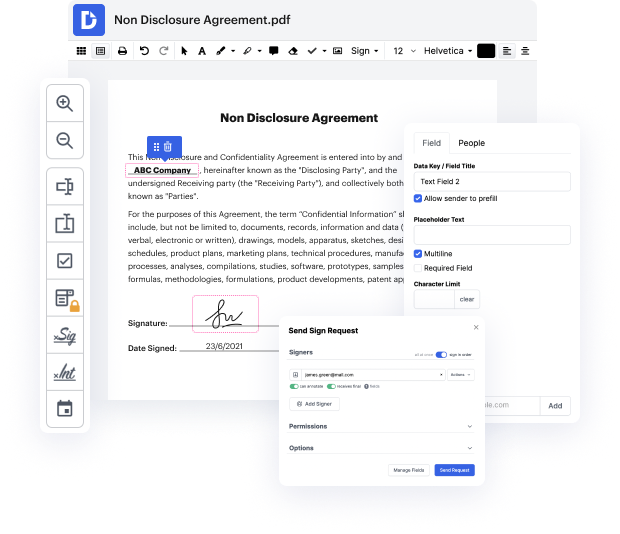
Our feature allows you to alter and edit papers, send data back and forth, create dynamic forms for information collection, encrypt and protect paperwork, and set up eSignature workflows. In addition, you can also generate templates from papers you utilize on a regular basis.
You’ll find plenty of additional tools inside DocHub, such as integrations that allow you to link your 602 form to a wide array of business programs.
DocHub is an intuitive, fairly priced option to manage papers and improve workflows. It provides a wide array of tools, from generation to editing, eSignature services, and web document developing. The software can export your documents in multiple formats while maintaining highest security and adhering to the maximum information protection requirements.
Give DocHub a go and see just how easy your editing transaction can be.
letamp;#39;s look at a common scenario that goes on many many times a day across all of our networks we need to log in to a device we need to log into an access point a vpn concentrator a firewall or some other device thatamp;#39;s connected to our network weamp;#39;ll send a request to that device with our username and our password but this device doesnamp;#39;t have a list of everyoneamp;#39;s username and password on it thereamp;#39;s a centralized database that has all of that information and itamp;#39;s contained on an authentication server so in order to check that we have the right username and password that device will send a message to the authentication server with our login credentials those credentials will be checked on the server and if our credentials do match whatamp;#39;s on the authentication server a message is sent back saying that those credentials are approved and that person can access this device now that our credentials have