

Disadvantages exist in every solution for editing every document type, and although you can find a wide variety of solutions out there, not all of them will suit your specific requirements. DocHub makes it much simpler than ever to make and alter, and manage papers - and not just in PDF format.
Every time you need to quickly negate recipient in xhtml, DocHub has got you covered. You can quickly modify document elements such as text and images, and structure. Customize, organize, and encrypt files, create eSignature workflows, make fillable forms for smooth data collection, and more. Our templates option enables you to generate templates based on papers with which you frequently work.
In addition, you can stay connected to your go-to productivity capabilities and CRM solutions while managing your files.
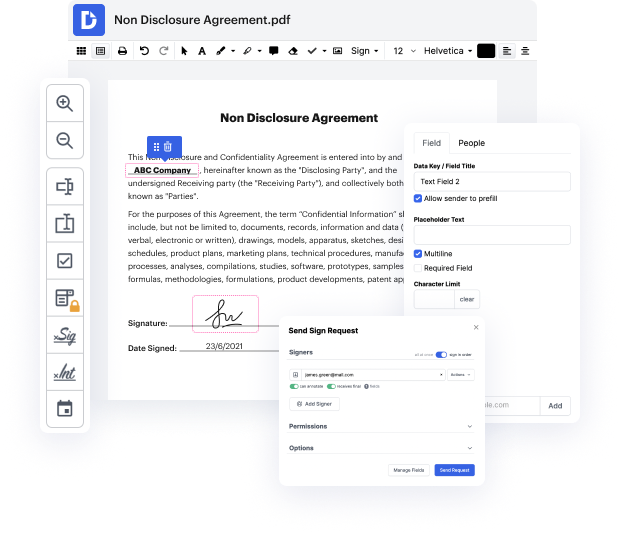
One of the most extraordinary things about leveraging DocHub is the ability to deal with document tasks of any difficulty, regardless of whether you require a swift edit or more diligent editing. It comes with an all-in-one document editor, website form builder, and workflow-centered capabilities. In addition, you can rest assured that your papers will be legally binding and adhere to all security protocols.
Cut some time off your projects by leveraging DocHub's capabilities that make managing files easy.
hey everyone so welcome back in this video weamp;#39;ll be solving another process scripting lab on putswick Academy so letamp;#39;s get started so this lab contains a reflected process scripting vulnerability in the search functionality but uses a vaf to protect against common xss vectors and to solve the slab we need to perform a crosstimpting attack that bypasses the map and calls the print function okay so we have a web that should be interesting and we need to somehow find a way to call the print function all right and we have a note as well a solution must not require any user interaction manually causing the print to be called in your own browser will not solve the lab okay fine now let me just head over to the lab right and this is the place where we have the croset scripting vulnerability correct and now like always whenever Iamp;#39;m trying to find a Crosshair scripting vulnerability the first thing that I do is Iamp;#39;ll always inject less than symbol right less than