

People often need to inlay identification in ACL when working with documents. Unfortunately, few applications offer the tools you need to complete this task. To do something like this typically involves changing between a couple of software programs, which take time and effort. Thankfully, there is a service that is applicable for almost any job: DocHub.
DocHub is a perfectly-developed PDF editor with a full set of useful capabilities in one place. Modifying, signing, and sharing documents gets simple with our online solution, which you can access from any internet-connected device.
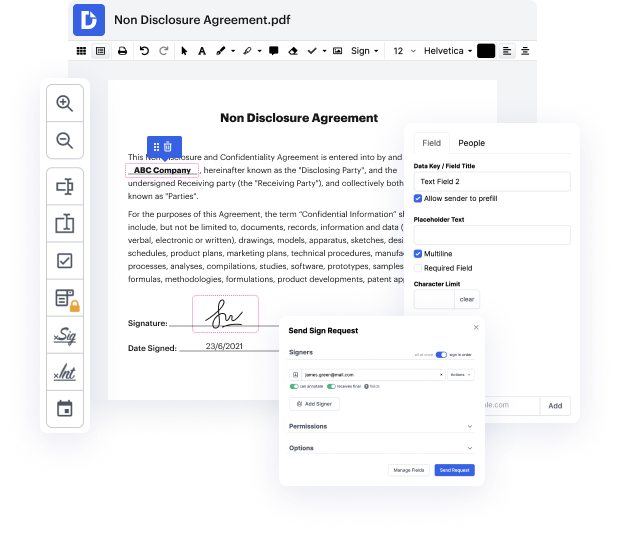
By following these five easy steps, you'll have your revised ACL rapidly. The user-friendly interface makes the process fast and productive - stopping jumping between windows. Try DocHub today!
hello everyone and welcome back what is Access Control list itamp;#39;s a set of rules defined for controlling Network traffic and reducing Network attacks ACL is used to filter incoming and outgoing Network traffic based on predefined rules or filtering criteria on a router device these rules are set by the network administrator he decides what information can come in and go out of the network these rules allow our deny specific traffic moving through the router ACL is at layer 3 security that controls the flow of traffic from one router to another it is also called a packet filtering firewalls ACL is configured on networking devices with packet filtering capabilities such as routers switches and firewalls where they act as filters or network gateways managing which traffic can access the network all right letamp;#39;s break it down into further details the main idea of using ACL is to provide security to computer network without it any traffic is either allowed to enter or exit mak