

Not all formats, including html, are developed to be quickly edited. Even though many tools can help us change all document formats, no one has yet invented an actual all-size-fits-all solution.
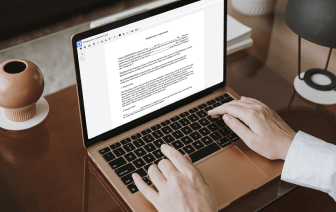
DocHub gives a easy and streamlined solution for editing, managing, and storing paperwork in the most popular formats. You don't have to be a technology-knowledgeable user to inject tone in html or make other modifications. DocHub is powerful enough to make the process straightforward for everyone.
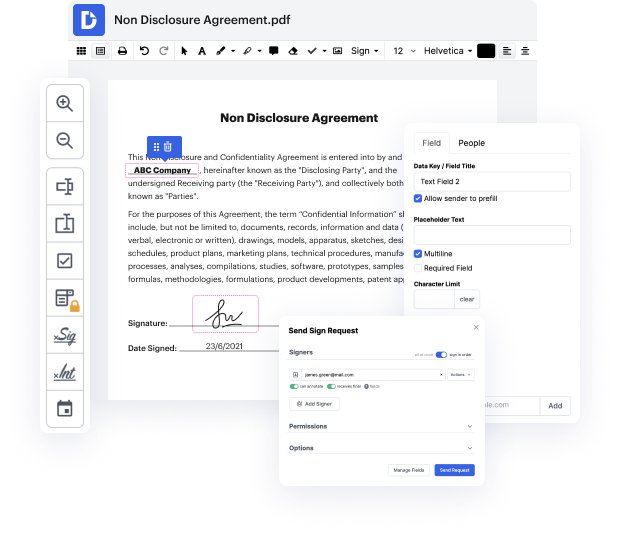
Our feature enables you to modify and edit paperwork, send data back and forth, generate dynamic documents for data gathering, encrypt and safeguard paperwork, and set up eSignature workflows. Additionally, you can also create templates from paperwork you use regularly.
You’ll find a great deal of other features inside DocHub, including integrations that allow you to link your html document to a wide array of business applications.
DocHub is a straightforward, fairly priced way to handle paperwork and streamline workflows. It offers a wide selection of capabilities, from generation to editing, eSignature professional services, and web document developing. The application can export your files in multiple formats while maintaining highest protection and following the maximum data safety requirements.
Give DocHub a go and see just how straightforward your editing operation can be.
so the heading for this section is called exploit the vulnerable code using HTML injections so first thing letamp;#39;s log in as the root user and then itamp;#39;s provide the password thatamp;#39;s shown in lab 4 once inside of here weamp;#39;re going to navigate to your bank comm and then weamp;#39;re going to illustrate a couple of things one thing weamp;#39;re going to illustrate is how the PHP code that we inserted inside of our custom homepage how itamp;#39;s susceptible to HTML injections the other thing weamp;#39;re going to do is weamp;#39;re going to discuss what it means to be vulnerable to this type of attack so first thing letamp;#39;s right-click letamp;#39;s view the page source inside the page source weamp;#39;re going to scroll down and weamp;#39;re gonna find that name attribute inside of our input field and again this is what our request function our PHP request function how it was referencing the data that was supplied to the username input field was b