

Not all formats, including html, are developed to be effortlessly edited. Even though numerous features will let us modify all document formats, no one has yet created an actual all-size-fits-all tool.
DocHub offers a easy and streamlined tool for editing, managing, and storing documents in the most widely used formats. You don't have to be a technology-savvy person to inject stamp in html or make other tweaks. DocHub is robust enough to make the process simple for everyone.
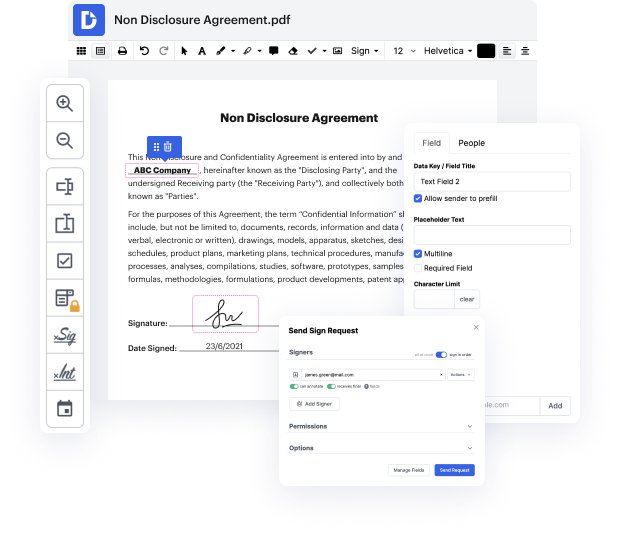
Our feature allows you to modify and tweak documents, send data back and forth, generate dynamic documents for information collection, encrypt and safeguard paperwork, and set up eSignature workflows. Moreover, you can also generate templates from documents you use on a regular basis.
You’ll locate plenty of other features inside DocHub, such as integrations that allow you to link your html document to various business programs.
DocHub is an intuitive, cost-effective way to deal with documents and streamline workflows. It offers a wide range of capabilities, from generation to editing, eSignature providers, and web form creating. The software can export your paperwork in multiple formats while maintaining greatest protection and following the greatest information safety requirements.
Give DocHub a go and see just how simple your editing process can be.
hey guys welcome back to the bug bounty series in this video weamp;#39;re going to be taking a look at html injection more specifically weamp;#39;re going to be taking a look at reflected hd html injection with the post request now as i mentioned weamp;#39;re going to be using a beatbox that contains b web and iamp;#39;m going to start it off you know chronologically within injection i know weamp;#39;ve taken a look at reflected injection with the get request we also took a look at iframe injection and php code injection so weamp;#39;ll be completing the rest of these various types of injections as we move along that being said letamp;#39;s get started so the first thing iamp;#39;m going to do is iamp;#39;m just going to click on the html injection reflected post using the post request so again this is a very very simple attack to understand uh in regards to the actual injection what is going to happen here is weamp;#39;re going to intercept the post request that is being sen