

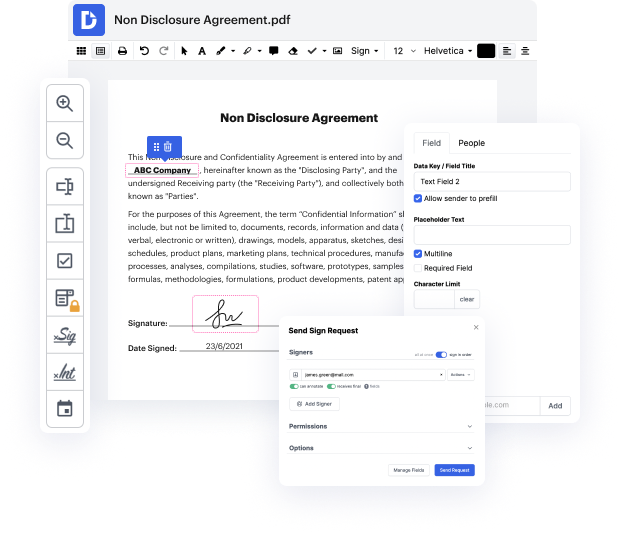
Regardless of how complex and difficult to modify your documents are, DocHub offers a simple way to modify them. You can modify any element in your xml without extra resources. Whether you need to tweak a single component or the entire document, you can rely on our robust solution for quick and quality results.
Moreover, it makes sure that the final document is always ready to use so that you’ll be able to get on with your tasks without any delays. Our all-encompassing set of capabilities also includes pro productivity tools and a library of templates, letting you make best use of your workflows without wasting time on recurring operations. On top of that, you can access your documents from any device and integrate DocHub with other solutions.
DocHub can take care of any of your document management operations. With a great deal of capabilities, you can create and export documents however you want. Everything you export to DocHub’s editor will be saved securely as much time as you need, with strict protection and information security protocols in place.
Try out DocHub today and make handling your documents simpler!
hello and welcome to secure code Vario in this module weamp;#39;ll be looking at expose and XML injections in this section will explain what these vulnerabilities are their causes and Preventionamp;#39;s and some potential hazards so what are XPath and XML injections these vulnerabilities are attacks that target XML data stores by injecting malicious XML and XPath code into user controllable input what causes XML or XPath injections these two types of injections are possible because user supplied input including cookies and other HTTP headers is not properly validated before being used as part of an XPath query or as part of data that will be stored in the XML data store to understand these vulnerabilities letamp;#39;s go through some examples first letamp;#39;s look at an XML injection which inserts unauthorized data here we have a website with an XML database containing user information the attacker will trick the website into creating a user with admin rights first the attacker