

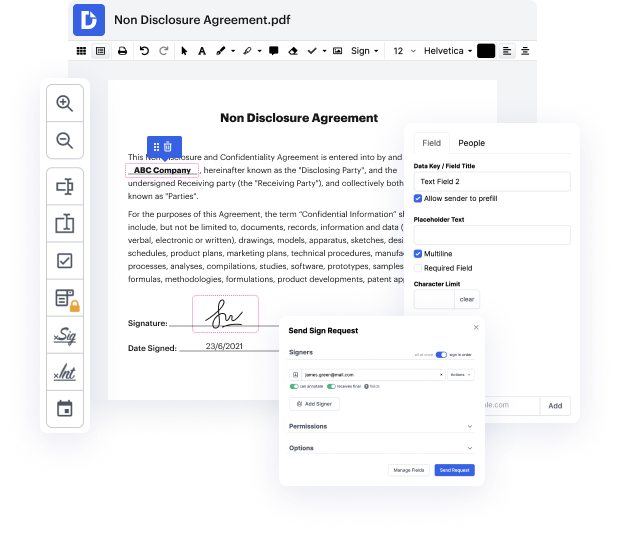
With DocHub, you can easily inject clause in SE from any place. Enjoy capabilities like drag and drop fields, editable textual content, images, and comments. You can collect eSignatures securely, include an additional layer of defense with an Encrypted Folder, and work together with teammates in real-time through your DocHub account. Make changes to your SE files online without downloading, scanning, printing or sending anything.
You can find your edited record in the Documents tab of your account. Prepare, send, print, or convert your file into a reusable template. With so many powerful features, it’s simple to enjoy trouble-free document editing and management with DocHub.
hi everyone welcome back to another video in the web security academy series in todayamp;#39;s video weamp;#39;ll be covering lab number one of the sql injection module so letamp;#39;s look at the description this lap contains a sql injection vulnerability in the product category filter so thatamp;#39;s important sql injection vulnerability and itamp;#39;s in the product category filter when the user selects a category the application carries out a sql query like the following so it actually gives us the backend sql query that gets executed which is great because we know the structure of the query that means we know how to automatically build our sql payload and weamp;#39;ll see that in a bit and then to solve the lab perform a sql injection attack that causes the application to display details of all products in any category both released and unreleased so the end goal is to display all products regardless of the category both released and unreleased so whatamp;#39;s likely hap