

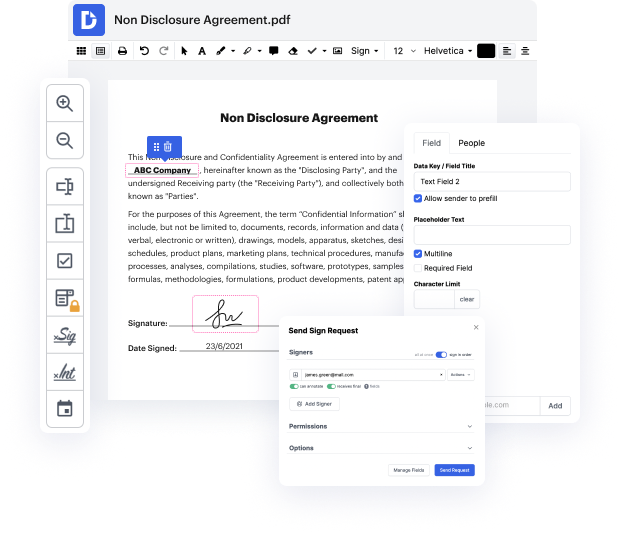
With DocHub, you can easily inject clause in cgi from anywhere. Enjoy capabilities like drag and drop fields, editable textual content, images, and comments. You can collect eSignatures safely, include an extra layer of defense with an Encrypted Folder, and collaborate with teammates in real-time through your DocHub account. Make changes to your cgi files online without downloading, scanning, printing or mailing anything.
You can find your edited record in the Documents tab of your account. Edit, share, print out, or convert your file into a reusable template. Considering the variety of powerful tools, it’s easy to enjoy seamless document editing and management with DocHub.
A code injection attack is when the attacker puts their own code into an existing data stream. This is often enabled because of bad programming with an application. An application shouldnamp;#39;t allow you to put your own code into a data stream. But, often, the code is not checked by the application, and attackers are able to exploit that vulnerability. Thereamp;#39;s many different types of code that you can inject. You can inject HTML, or LDAP, or SQL code-- and any one of those may be able to manipulate or gather information from a machine, especially if you have control over the type of code that you would put into that data stream. One very common code injection type is a SQL injection. SQL stands for Structured Query Language-- or SQL. This is a very common relational database used on many websites. If you can circumvent the web front end, then you can gain access to the data thatamp;#39;s in that database. Of course, the web front end should not allow these types of request