

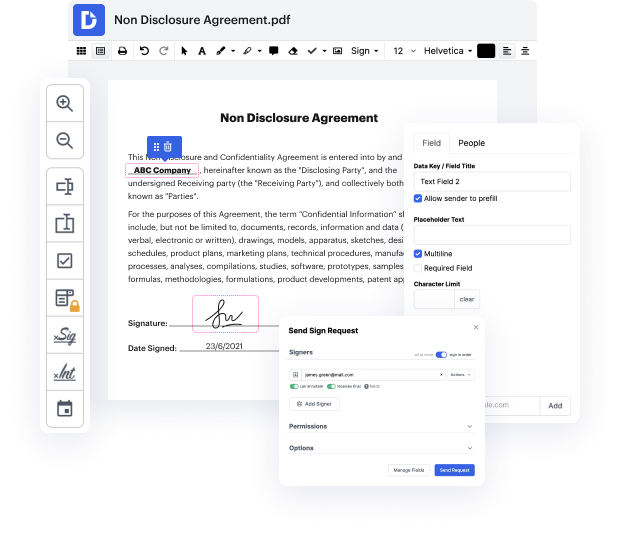
People frequently need to inject authentication in DOTX when managing documents. Unfortunately, few programs provide the features you need to complete this task. To do something like this normally involves switching between multiple software applications, which take time and effort. Luckily, there is a service that is applicable for almost any job: DocHub.
DocHub is an appropriately-developed PDF editor with a complete set of valuable features in one place. Altering, approving, and sharing forms becomes straightforward with our online solution, which you can use from any online device.
By following these five basic steps, you'll have your adjusted DOTX quickly. The intuitive interface makes the process fast and efficient - stopping switching between windows. Start using DocHub today!
if a web application does not properly validate the host header value in the http request then it might be vulnerable to http host header injection attacks during this video we look at a simple scenario where an attacker injects a malicious payload into the http host header to bypass application access control to perform administrative actions without having valid admin credentials for the purpose of this video we use a lab from web security academy called host header authentication bypass and you can find the link to this lab in the video description to solve this lab we need to access the admin panel and then delete user colors alright letamp;#39;s get started by clicking on access to lab from the lab description we know the application has an admin panel but we donamp;#39;t know the url for accessing this panel letamp;#39;s see if we can find any information about the admin panel url from the robots.txt file so we go to the address bar and add slash robots.txt at the end of the u