

Choosing the best file administration solution for the firm can be time-consuming. You need to assess all nuances of the platform you are interested in, compare price plans, and stay vigilant with security standards. Arguably, the opportunity to work with all formats, including EZW, is essential in considering a solution. DocHub offers an substantial list of functions and tools to successfully manage tasks of any complexity and take care of EZW formatting. Get a DocHub account, set up your workspace, and begin dealing with your documents.
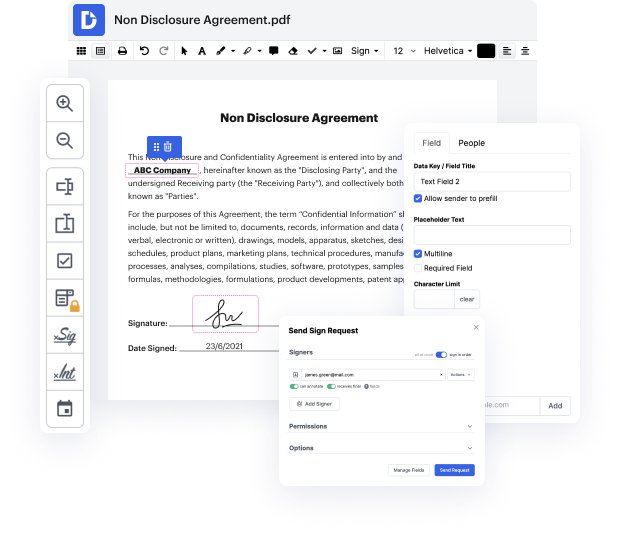
DocHub is a comprehensive all-in-one app that permits you to edit your documents, eSign them, and create reusable Templates for the most commonly used forms. It provides an intuitive interface and the opportunity to deal with your contracts and agreements in EZW formatting in the simplified mode. You don’t have to bother about reading countless guides and feeling anxious because the software is way too complex. include token in EZW, delegate fillable fields to chosen recipients and gather signatures quickly. DocHub is about powerful functions for professionals of all backgrounds and needs.
Boost your file generation and approval operations with DocHub right now. Benefit from all this with a free trial version and upgrade your account when you are ready. Modify your documents, generate forms, and discover everything that you can do with DocHub.
want to know more about refresh tokens and how to store them securely then keep watching this video because Ill be covering both topics [Music] hey everyone Im will Im a developer advocate here at off zero in this video Im going to talk about refresh tokens as they are defined in oauth 2.0 youll learn about how refresh tokens compare against the other two token types and how they balance security usability and privacy but first lets talk about what is a token what is a token tokens are pieces of data with just enough information to carry out the process of determining the users Identity or authorizing the user to perform an action tokens are artifacts that allow applications to perform the authorization and authentication processes some identity Frameworks and protocols use token-based strategies to secure access to applications and resources for example we use oauth 2.0 for authorization and openid connect for Authentication oauth 2.0 allows an application to access resources