

Not all formats, including binary, are created to be easily edited. Even though many capabilities will let us tweak all file formats, no one has yet created an actual all-size-fits-all tool.
DocHub offers a simple and streamlined tool for editing, taking care of, and storing documents in the most widely used formats. You don't have to be a technology-savvy person to faint certificate in binary or make other modifications. DocHub is robust enough to make the process straightforward for everyone.
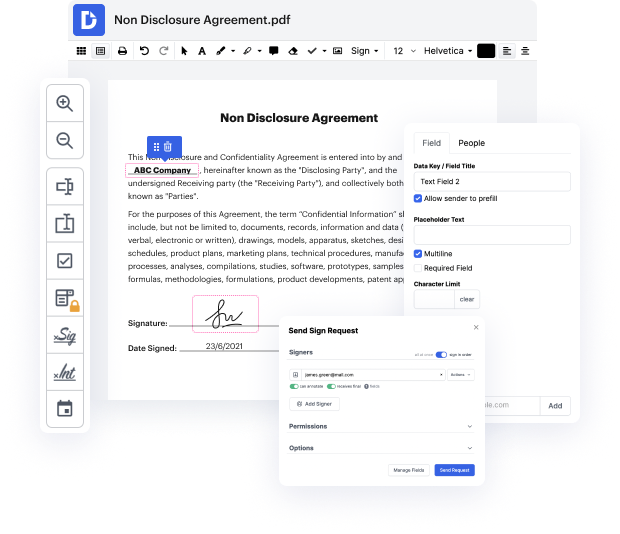
Our feature enables you to change and edit documents, send data back and forth, generate interactive forms for data gathering, encrypt and shield paperwork, and set up eSignature workflows. Moreover, you can also create templates from documents you utilize frequently.
You’ll find a great deal of other functionality inside DocHub, such as integrations that allow you to link your binary file to a variety productivity programs.
DocHub is a straightforward, fairly priced option to deal with documents and streamline workflows. It offers a wide range of features, from creation to editing, eSignature providers, and web form developing. The software can export your files in many formats while maintaining highest security and adhering to the highest data security criteria.
Give DocHub a go and see just how straightforward your editing process can be.
weamp;#39;re now going to talk about a term called the chain of trust as it applies to SSL Certificates and to start their discussion weamp;#39;ll revisit our look at our root certificate authorities root CA now root CA s their certificates have to be kept behind numerous layers of security because the private keys of root certificates are we have to make sure that theyamp;#39;re absolutely inaccessible if the private keys are compromised in all the certificates based on a root CA are compromised as well so we often use a stand-in for root certificate or proxy something called an intermediate CA so these are entities or organizations that can issue certificates and whose certificate themselves is signed by root CA so letamp;#39;s suppose we look at our organization NSCC CA it can now make a certificate signing request to an intermediate CA so weamp;#39;ll just call this I ca now what happens when an I ca can actually issue actually a chain of certificates to an SEC so weamp;#39;l