

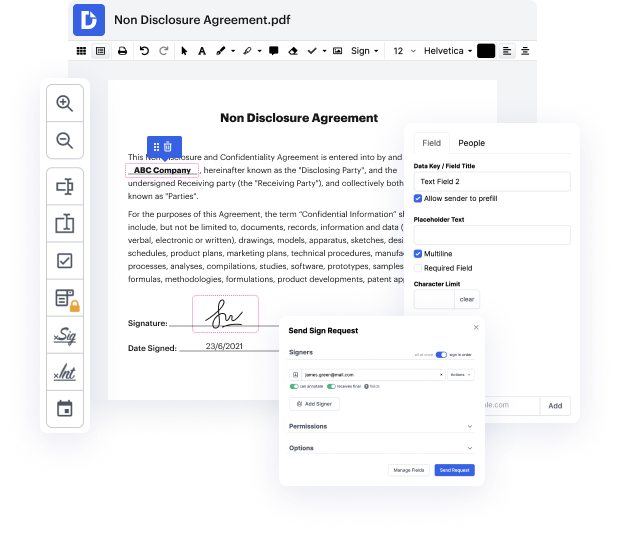
Not all formats, including DOCM, are developed to be easily edited. Even though numerous capabilities can help us modify all form formats, no one has yet invented an actual all-size-fits-all tool.
DocHub offers a simple and efficient tool for editing, taking care of, and storing documents in the most widely used formats. You don't have to be a technology-knowledgeable user to faint authentication in DOCM or make other changes. DocHub is powerful enough to make the process easy for everyone.
Our tool allows you to alter and edit documents, send data back and forth, create interactive documents for information gathering, encrypt and protect forms, and set up eSignature workflows. Additionally, you can also create templates from documents you utilize regularly.
You’ll locate a great deal of additional tools inside DocHub, including integrations that allow you to link your DOCM form to different business apps.
DocHub is a straightforward, cost-effective option to manage documents and improve workflows. It provides a wide range of capabilities, from creation to editing, eSignature solutions, and web document building. The software can export your documents in multiple formats while maintaining highest safety and adhering to the highest information security criteria.
Give DocHub a go and see just how easy your editing operation can be.
hey everybody john wagner here with dev central and weamp;#39;re going through the 2021 owasp top 10 security risks and coming in at number seven is identification and authentication failures all right so this deals with um identification authentication so this was previously known as broken authentication uh and this has slid down the list from the 2017 it was in the second it was number two on the 2017 so now itamp;#39;s slid down to number seven but nonetheless itamp;#39;s still on the top ten and itamp;#39;s still a big deal right so this obviously deals with users identity authentication session session management all of these things are critical to uh to protect against these authentication related attacks right so you know if you have an application uh you know just put your app right here youamp;#39;ve got you know users that want to access your application and there needs to be some kind of you know authentication mechanism that happens to make sure hey are you um