


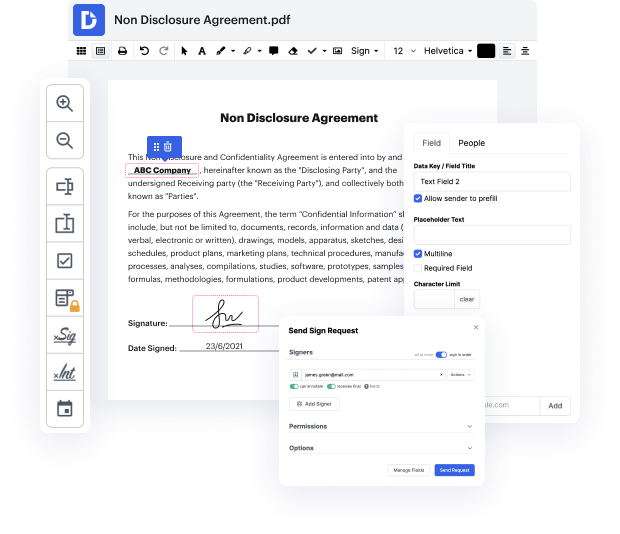
Getting full control over your files at any time is crucial to ease your day-to-day duties and enhance your efficiency. Achieve any goal with DocHub tools for papers management and convenient PDF file editing. Gain access, change and save and incorporate your workflows with other secure cloud storage.
DocHub gives you lossless editing, the chance to use any format, and safely eSign papers without searching for a third-party eSignature software. Maximum benefit from the file managing solutions in one place. Consider all DocHub capabilities today with the free account.
In this lesson, we explore asymmetric encryption, which utilizes a key pair for encryption and decryption. Each participant, Pam and Jim, possesses their own public and private keys. Pam’s public key is accessible to Jim, while her private key remains confidential. Conversely, Jim has his own set of keys. The essential principle of asymmetric encryption is that a message encrypted with one party's public key can only be decrypted using the corresponding private key and vice versa. This ensures secure data exchange between Pam and Jim using their respective key pairs.