

Flaws are present in every tool for editing every file type, and despite the fact that you can use a wide variety of tools on the market, not all of them will fit your specific needs. DocHub makes it much simpler than ever to make and modify, and deal with paperwork - and not just in PDF format.
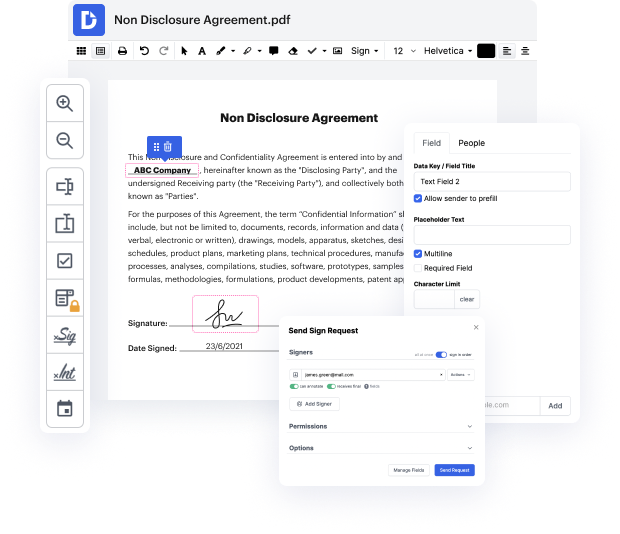
Every time you need to quickly cut authentication in PAP, DocHub has got you covered. You can easily modify form components including text and pictures, and structure. Personalize, organize, and encrypt paperwork, build eSignature workflows, make fillable documents for stress-free information gathering, etc. Our templates option allows you to generate templates based on paperwork with which you frequently work.
Additionally, you can stay connected to your go-to productivity features and CRM platforms while managing your paperwork.
One of the most remarkable things about utilizing DocHub is the ability to manage form activities of any complexity, regardless of whether you require a fast tweak or more complex editing. It includes an all-in-one form editor, website form builder, and workflow-centered features. Additionally, you can be certain that your paperwork will be legally binding and comply with all safety frameworks.
Cut some time off your projects with DocHub's features that make handling paperwork straightforward.
hi and welcome in this video Iamp;#39;ll discuss the three network authentication protocols which operates at layer 2 of the OSI model that is the return link layer now a network authentication protocol basically authenticates the claim of a client once it wants to connect to a network and a good network security design should assume that an attacker can sniff all the network traffic now the first protocol is the parent occation protocol which is a very weak indication protocol because it sends the username and password in clear text so any attacker can sniff the information and can launch a replay attack by replaying these information so this protocol is very weak and should not be used now the next protocol is the challenge handshake authentication protocol or chair now this protocol is more secure because it does not share the password on the network in clear text and passwords are created during the account enrollment process of a client and these passwords are only stored over th