

Not all formats, such as DBK, are developed to be easily edited. Even though numerous capabilities can help us edit all document formats, no one has yet created an actual all-size-fits-all solution.
DocHub provides a simple and streamlined solution for editing, managing, and storing papers in the most widely used formats. You don't have to be a technology-savvy user to cut authentication in DBK or make other modifications. DocHub is robust enough to make the process easy for everyone.
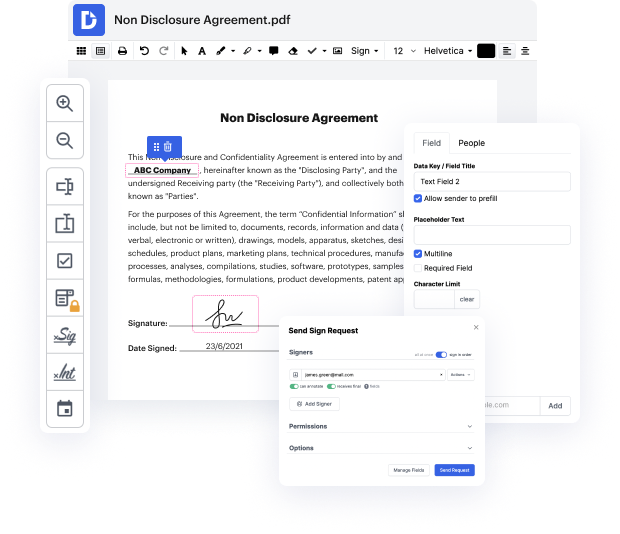
Our tool allows you to modify and edit papers, send data back and forth, create dynamic forms for data gathering, encrypt and shield paperwork, and set up eSignature workflows. In addition, you can also create templates from papers you use regularly.
You’ll find a great deal of additional tools inside DocHub, such as integrations that let you link your DBK document to different productivity applications.
DocHub is a straightforward, fairly priced option to deal with papers and streamline workflows. It offers a wide array of tools, from generation to editing, eSignature services, and web document developing. The application can export your files in multiple formats while maintaining maximum protection and following the maximum data safety criteria.
Give DocHub a go and see just how easy your editing process can be.
and welcome back in the authentication phase of aaa we have some fantastic technical options for validating who the user is one of those options is of course to use a password now passwords however can be problematic because if an attacker learns or steals a password the attacker could use that password to impersonate the user also suppose we have a password that is used with plain text protocols including http ftp or other protocols such as password authentication protocol or pap which you can use on the back end iamp;#39;ll talk more about that in just a moment in those cases where weamp;#39;re using a password with plain text protocols that password could be compromised just by somebody eavesdropping or sniffing the network so hereamp;#39;s an example of that imagine we have bob here and bob is at his computer which is connected to this port on the switch and letamp;#39;s imagine also that weamp;#39;re doing 802.1x in this environment which basically means we want to make bob p