

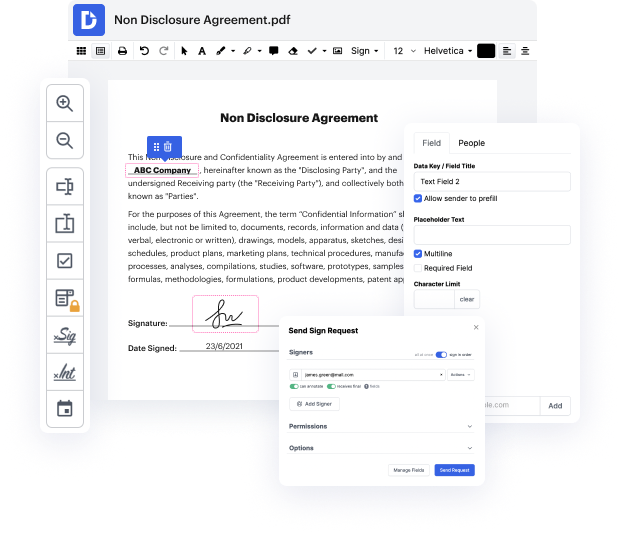
Our platform offers an intuitive approach to digital document management, making it easier than ever to create, edit, and sign documents online for free. With a deep integration with Google Workspace, users can seamlessly import, export, and modify documents directly from Google apps. This functionality ensures smooth business processes and interactive workflows, allowing you to manage your documents efficiently.
Start creating and signing your digital documents with ease today!
ld then tend to do is generate a symmetric key and use that to encrypt the message and then we would encrypt that symmetric key with the recipient's public key so we're still using a public private key encryption but we're using it just to encrypt a tiny piece of information which is the symmetric key which is much quicker and a lot more practical for long messages so what tends to happen is when you get a certificate one of the things in it is a public key and this is what this video is about we want to talk about how that public key actually comes about so when you generate a public key you generate a pair of keys which are based on prime numbers and things like that theyre actually quite a complicated process through a series of mathematical algorithms and interactions that generate these keys and when you do that you get a public key and a private key and in the terms of public key infrastructures we want to look at where these keys get created.
At DocHub, your data security is our priority. We follow HIPAA, SOC2, GDPR, and other standards, so you can work on your documents with confidence.
Learn more



