

Flaws are present in every tool for editing every file type, and although you can find a wide variety of tools on the market, not all of them will suit your specific requirements. DocHub makes it easier than ever to make and change, and manage papers - and not just in PDF format.
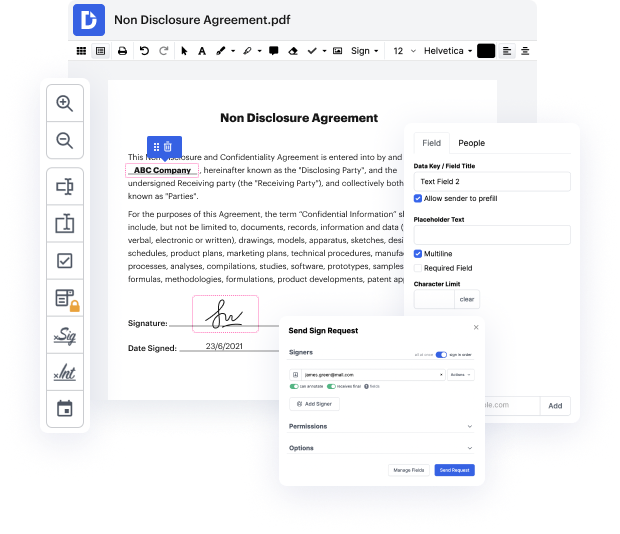
Every time you need to quickly cover up payee in CWK, DocHub has got you covered. You can effortlessly alter form components including text and images, and structure. Customize, arrange, and encrypt files, build eSignature workflows, make fillable documents for smooth information collection, etc. Our templates feature enables you to create templates based on papers with which you frequently work.
Additionally, you can stay connected to your go-to productivity tools and CRM solutions while dealing with your files.
One of the most remarkable things about leveraging DocHub is the ability to deal with form activities of any difficulty, regardless of whether you require a fast edit or more diligent editing. It comes with an all-in-one form editor, website document builder, and workflow-centered tools. Additionally, you can be sure that your papers will be legally binding and adhere to all security frameworks.
Shave some time off your tasks with the help of DocHub's features that make handling files straightforward.
last time we talked about how you can secure your service accounts by understanding the iam roles associated with them one of the roles i mentioned was a service account key admin a role that lets you create service account keys that could then be used to allow users to authenticate as a service account from outside google cloud that sounds kind of risky doesnamp;#39;t it today iamp;#39;ll go over a few fundamentals of managing service account keys so that you can reduce the risk and keep your service account safe and in case you want to minimize using service account keys iamp;#39;ll show you how in some cases you can authenticate as a service account without having to create or distribute keys at all letamp;#39;s get to it iamp;#39;m going to tell you whatamp;#39;s what with service count keys and impersonation before we dive into service account keys letamp;#39;s talk about the security implication of using them for users that already have access to your project there arenam