

Not all formats, including xht, are created to be effortlessly edited. Even though numerous capabilities can help us modify all form formats, no one has yet created an actual all-size-fits-all solution.
DocHub offers a straightforward and streamlined solution for editing, taking care of, and storing documents in the most popular formats. You don't have to be a technology-knowledgeable person to conceal URL in xht or make other modifications. DocHub is powerful enough to make the process simple for everyone.
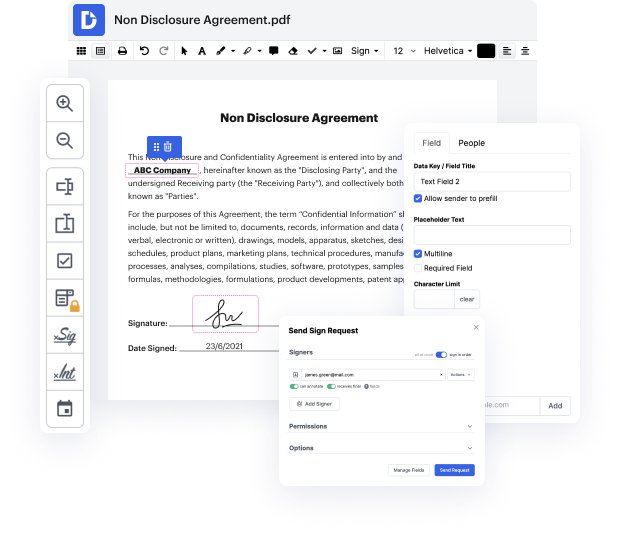
Our tool enables you to modify and edit documents, send data back and forth, generate dynamic documents for information collection, encrypt and shield documents, and set up eSignature workflows. In addition, you can also generate templates from documents you utilize regularly.
You’ll locate a great deal of other functionality inside DocHub, including integrations that allow you to link your xht form to various business apps.
DocHub is a simple, fairly priced option to manage documents and improve workflows. It provides a wide array of tools, from creation to editing, eSignature services, and web form building. The application can export your documents in many formats while maintaining highest safety and adhering to the highest information safety requirements.
Give DocHub a go and see just how simple your editing transaction can be.
in a previous video we talked about how fishing attack unrolls step by step from the initial access through either email or text message or phone call into either URL attachment and then potentially added into malware explore it or fishing website we also covered how different techniques like a type of squatting or abusing subdomain or URL path used by attacker to try to imitate a benign URL inside official benign domain inside the fusion URL today weamp;#39;re going to talk about more Advanced Techniques which would most likely used in a target attack to actually completely hide a phishing URL and make it look like a legitimate one an exact copy of legitimate URL to fool a victim to believe that the victim is visiting a legitimate website sometimes especially in in a target attack in a spearfishing an attacker cannot afford to play by chance so they want the URL to look exactly like a benign website thereamp;#39;s a couple of techniques published by the security researcher with the