

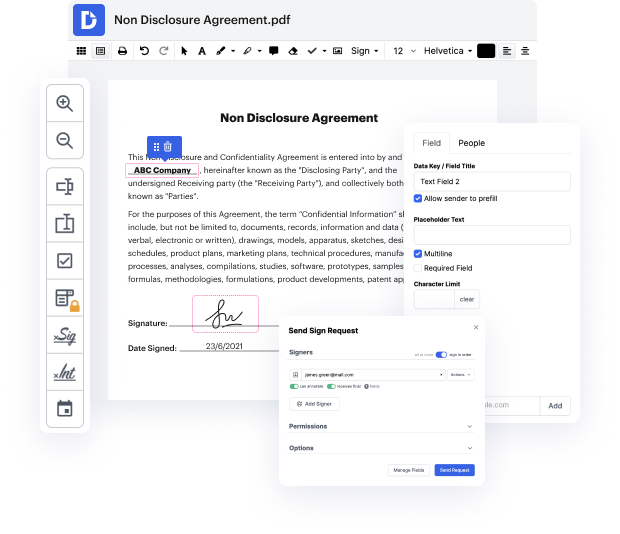
You no longer have to worry about how to clean up personal information in Radix-64. Our powerful solution provides easy and quick document management, allowing you to work on Radix-64 files in a couple of minutes instead of hours or days. Our service includes all the tools you need: merging, inserting fillable fields, approving forms legally, placing shapes, and so on. You don't need to install additional software or bother with expensive programs demanding a powerful device. With only two clicks in your browser, you can access everything you need.
Start now and handle all various types of forms professionally!
Hi and welcome to the Azure Sentinel notebooks channel, my name is Jannie Li and I am a Software Engineer on the Microsoft Threat Intelligence team. Today Iamp;#39;m going to be talking about the guided hunting Base64 encoded Linux commands notebook. This notebook is a collection of tools for detecting malicious behavior on Linux machines, when commands are Base64 encoded. This behavior is commonly seen in crypto mining attacks. The notebook allows you to specify a workspace and highlights as well as categorizes potential malicious behavior within that workspace, allowing you to hunt and pivot on key entities. The notebook primarily utilizes Azure Sentinel Syslog data and telemetry from the MSTIC research branch of the AUOMS tool. Details on how to set those up as well as an in-depth written guide on the notebook are available in the description below, as well as on the Microsoft TechCommunity blog. To launch notebooks simply find it in the notebooks tab
At DocHub, your data security is our priority. We follow HIPAA, SOC2, GDPR, and other standards, so you can work on your documents with confidence.
Learn more



