

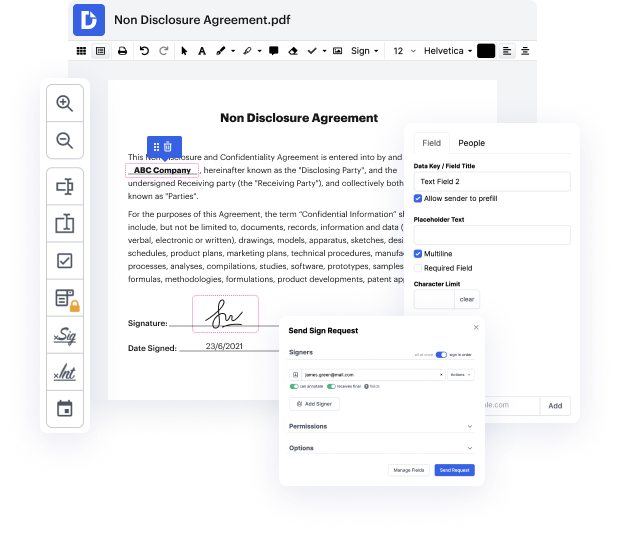
Regardless of how labor-intensive and difficult to change your files are, DocHub provides a simple way to modify them. You can change any element in your Radix-64 with no extra resources. Whether you need to modify a single component or the whole document, you can entrust this task to our powerful solution for fast and quality results.
Moreover, it makes sure that the final document is always ready to use so that you’ll be able to get on with your tasks without any slowdowns. Our all-encompassing group of capabilities also comes with pro productivity tools and a catalog of templates, enabling you to make best use of your workflows without wasting time on repetitive activities. Moreover, you can gain access to your papers from any device and incorporate DocHub with other apps.
DocHub can handle any of your document management activities. With an abundance of capabilities, you can generate and export paperwork however you prefer. Everything you export to DocHub’s editor will be saved safely for as long as you need, with strict safety and information protection frameworks in place.
Check DocHub now and make handling your paperwork more seamless!
hi all uh Iamp;#39;m shik munar assistant professor of sanan engineering College year andit so today Iamp;#39;m going to discuss about radic 64 conversion actually this radic 64 conversion is used in pgp that is a pretty good privacy and pgp provides a confidentiality and authentication Service that can be used for electronic mail and file storage applications as a part of providing the confidentiality email data has to be encrypted and the encrypted data may have some non printable aski characters but email systems only permit the use of ask text that means the encrypted email may not have all aski characters we need to have a mechanism which converts the non-printable aski characters into a printable asky characters so it is the responsibility of the radic 64 conversion or the radic 64 conversion functionality is to convert the non-printable husy characters into printable aski characters this technique is used in both pgp and yes M this technique Maps the arbitrary binary input int