

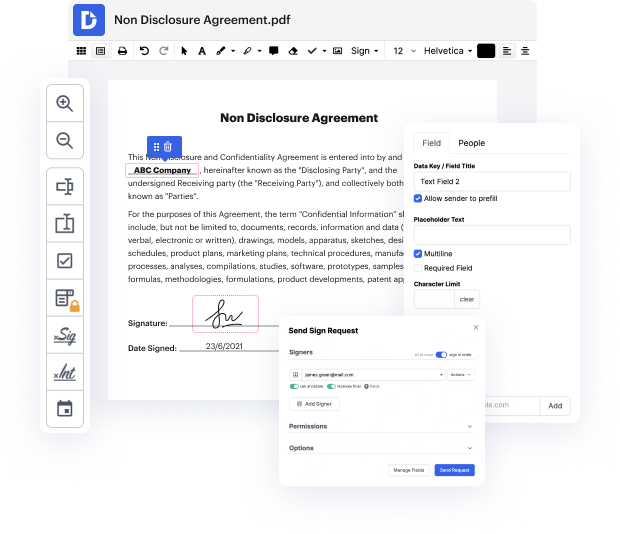
DocHub allows you to change signature in IT Service Request quickly and conveniently. No matter if your form is PDF or any other format, you can effortlessly alter it leveraging DocHub's user-friendly interface and powerful editing capabilities. With online editing, you can alter your IT Service Request without downloading or setting up any software.
DocHub's drag and drop editor makes personalizing your IT Service Request simple and efficient. We securely store all your edited papers in the cloud, letting you access them from anywhere, whenever you need. On top of that, it's straightforward to share your papers with parties who need to check them or add an eSignature. And our native integrations with Google products enable you to transfer, export and alter and endorse papers right from Google applications, all within a single, user-friendly program. In addition, you can quickly turn your edited IT Service Request into a template for repeated use.
All completed papers are securely stored in your DocHub account, are easily managed and shifted to other folders.
DocHub simplifies the process of completing form workflows from day one!
The point of public key encryption is that the public key component is really public. That is, any user can send his or her public key to any other user or just broadcast it to the world. Although this approach is very convenient, it has a major weakness. That is, anyone can forge such a public announcement. Some user could pretend to be Bob, and send a public key to another user such as Alice, and tell Alice that this is Bobs public key. The result is that when Alice sends a private message to Bob saying she encrypts it using Bobs public key. But remember this Bobs public key is actually forged by the attacker. Then the message can be intercepted by the attacker, and can be read by the attacker. Now, at some point hopefully, Bob can discover that theres a forgery going on and a public key of his was being used. But then what can Bob do? Bob can send Alice another message saying that, hey, this is my real public key. But how could Alice tell? That is, how could Alice tell that the