

Not all formats, including xht, are designed to be effortlessly edited. Even though numerous tools can help us edit all form formats, no one has yet invented an actual all-size-fits-all solution.
DocHub provides a simple and efficient solution for editing, handling, and storing documents in the most widely used formats. You don't have to be a tech-savvy user to blot epitaph in xht or make other modifications. DocHub is robust enough to make the process easy for everyone.
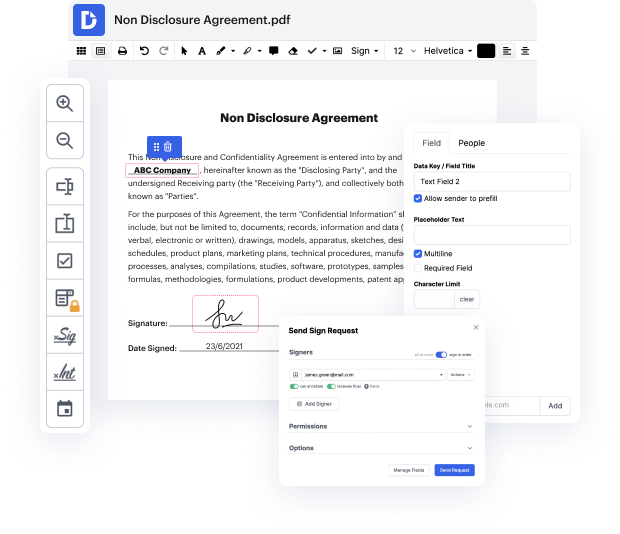
Our feature allows you to alter and edit documents, send data back and forth, create interactive forms for data collection, encrypt and safeguard paperwork, and set up eSignature workflows. Additionally, you can also generate templates from documents you utilize regularly.
You’ll find a great deal of additional tools inside DocHub, such as integrations that let you link your xht form to a variety productivity programs.
DocHub is an intuitive, cost-effective option to manage documents and simplify workflows. It provides a wide selection of features, from generation to editing, eSignature solutions, and web form building. The software can export your paperwork in multiple formats while maintaining highest protection and following the highest data protection standards.
Give DocHub a go and see just how easy your editing process can be.
so natus 19 from the over the wire war game starts out in the prompt and page telling us that this page uses most of the same code as the previous level level 18 but such an IDs are no longer sequential it gives us the prompt to please log in with your admin account to retrieve credentials for the next level not as 20 and we see this form with the HTTP POST method to index dot PHP but there is no link to view the source code in this level so weamp;#39;re just gonna have to operate under the assumption that again this page uses most of the same code as a previous level so in our Python code letamp;#39;s actually take a look at what we have here after we make this request we can see what our session cookies are because weamp;#39;re using a session to request this page we should be able to determine what the actual cookies are following this so we can print out session cookies and letamp;#39;s go ahead and check out the output right now it should be nothing because we havenamp;#39;t