

Flaws are present in every tool for editing every file type, and despite the fact that you can find a wide variety of tools out there, not all of them will fit your specific needs. DocHub makes it easier than ever to make and alter, and handle papers - and not just in PDF format.
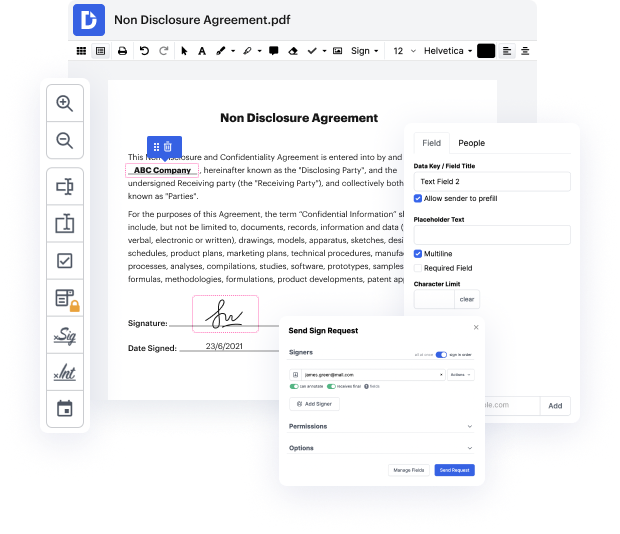
Every time you need to quickly black out sample in xht, DocHub has got you covered. You can easily modify document elements including text and images, and layout. Customize, organize, and encrypt paperwork, build eSignature workflows, make fillable documents for smooth information gathering, etc. Our templates option allows you to create templates based on papers with which you frequently work.
Moreover, you can stay connected to your go-to productivity capabilities and CRM solutions while managing your paperwork.
One of the most remarkable things about leveraging DocHub is the ability to handle document activities of any complexity, regardless of whether you require a swift tweak or more diligent editing. It includes an all-in-one document editor, website form builder, and workflow-centered capabilities. Moreover, you can rest assured that your papers will be legally binding and adhere to all protection protocols.
Cut some time off your tasks by leveraging DocHub's tools that make managing paperwork easy.
and youamp;#39;re here for talk entitled abusing xslt for practical attacks your speaker is Fernando Arnel Baldy thank you hello thank you for coming today and thank you black and for the invitation my name is Fernando Nibali and they work as a security consultant on researcher for ioactive I would like to show you today how accessibility implementations are vulnerable to multiple practical attacks for that matter the very first question that I would like to address today will be this one why are we talking about what xslt a couple of years ago I was working with a real scientist a co-worker from ioactive on a penetration test and he discovered an external entity expansion attack they are pretty common we are here this year black and we have two presentations related to those type of vulnerabilities so I decided to explore a little bit more about the topic to learn a little bit more about XML schemas and xslt who somehow all these technologies may work together the objectives of this