


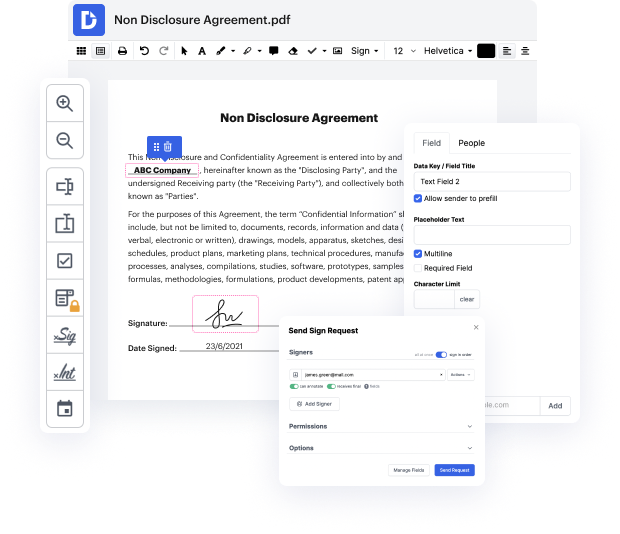
Many people find the process to black out evidence in HWPML rather challenging, particularly if they don't frequently deal with documents. However, these days, you no longer have to suffer through long tutorials or spend hours waiting for the editing software to install. DocHub allows you to modify forms on their web browser without setting up new programs. What's more, our robust service provides a full set of tools for professional document management, unlike so many other online solutions. That’s right. You no longer have to donwload and re-upload your forms so often - you can do it all in one go!
No matter what type of paperwork you need to adjust, the process is easy. Make the most of our professional online service with DocHub!
penetration testers as well as blackhat hackers look for vulnerabilities and websites both groups use the same processes and automated tools to achieve very different goals like clever thieves looking for points of entry except digital spying isnamp;#39;t carried out by people itamp;#39;s done by launching reconnaissance missions using hacker tools to gather valuable Intel fast Oh wasp calls this vulnerability identification fingerprinting and footprinting are like casing the joint vulnerability scanning identifies the point of entry fingerprinting checks the foundation of a site what server and software is running automated tools also known as BOTS identified the nuts and bolts of the website then flip printing takes an inventory of the entire attack surface of the web application looking for weak spots by analyzing pages directory names apiamp;#39;s URL paths and all other resources now that the attacker understands the structure and technology used on the website it can m