

Flaws are present in every tool for editing every file type, and despite the fact that you can use a lot of solutions on the market, not all of them will suit your specific requirements. DocHub makes it easier than ever to make and modify, and handle papers - and not just in PDF format.
Every time you need to swiftly tweak account in LOG, DocHub has got you covered. You can quickly alter form elements such as text and pictures, and layout. Personalize, organize, and encrypt files, build eSignature workflows, make fillable documents for intuitive data gathering, and more. Our templates option allows you to create templates based on papers with which you frequently work.
Moreover, you can stay connected to your go-to productivity tools and CRM solutions while dealing with your files.
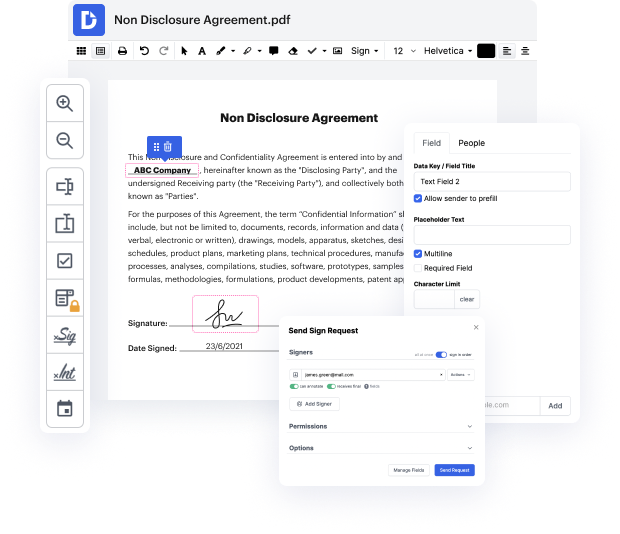
One of the most remarkable things about leveraging DocHub is the ability to handle form activities of any difficulty, regardless of whether you need a swift modify or more diligent editing. It includes an all-in-one form editor, website document builder, and workflow-centered tools. Moreover, you can be certain that your papers will be legally binding and adhere to all protection protocols.
Shave some time off your projects with DocHub's tools that make handling files straightforward.
thank you hello again everyone and welcome back to learn Linux TV in todayamp;#39;s video weamp;#39;re going to take a look at five different tweaks that you can Implement in your Linux server to better protect openssh from outside threats open SSH itself is a very awesome technology because itamp;#39;s pretty much the closest standard that we have in the Linux Community when it comes to Remote Management you could use SSH to connect to your Linux server from just about anywhere with internet access and then you can issue commands to your server as if you are standing right in front of it but unfortunately if someone else takes control of openssh and gets access to your server well thatamp;#39;s not a good day we donamp;#39;t want that to happen so in this video like I mentioned Iamp;#39;m going to go over five different methods that you can utilize to better protect openssh on your Linux server now if youamp;#39;ve already seen my other videos on this topic my older videos on t