

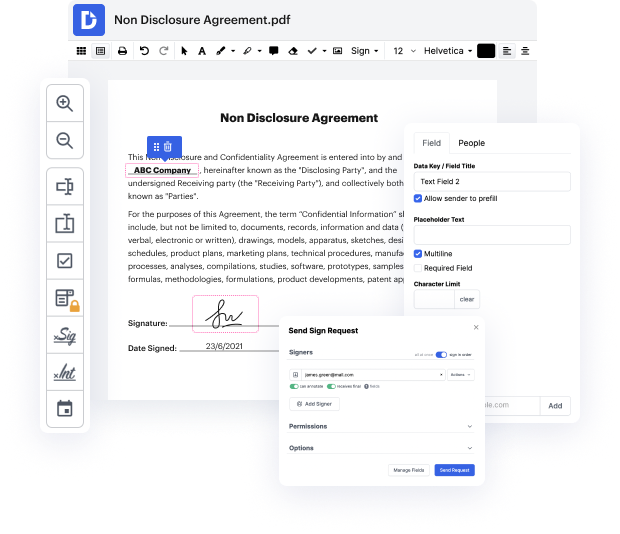
xht may not always be the easiest with which to work. Even though many editing features are out there, not all offer a simple tool. We developed DocHub to make editing effortless, no matter the file format. With DocHub, you can quickly and effortlessly strike pecularity in xht. In addition to that, DocHub provides a range of other features such as form creation, automation and management, field-compliant eSignature tools, and integrations.
DocHub also lets you save time by creating form templates from documents that you use frequently. In addition to that, you can make the most of our numerous integrations that allow you to connect our editor to your most utilized programs effortlessly. Such a tool makes it quick and easy to work with your documents without any delays.
DocHub is a useful tool for personal and corporate use. Not only does it offer a all-encompassing set of features for form creation and editing, and eSignature integration, but it also has a range of features that prove useful for developing complex and straightforward workflows. Anything uploaded to our editor is kept secure according to major field requirements that protect users' data.
Make DocHub your go-to choice and simplify your form-based workflows effortlessly!
cobbled strike is a red team tool that is used for penetration tests at least this is what it was created to be used for instead it is commonly used by red teamers but has also been cracked and leaked online where threat actors will make use of cobbleamp;#39;s strike within unauthorized penetration tests against companies Nationwide these three actors will use it to bypass EDR and antiviruses and then it is commonly used in penetrations against large companies where ransomware is the final payload cobblestrike is a great tool to be used for these scenarios because it is built to be used Within These environments it can be used along with different kinds of C2 profiles such as malleable c2s and what these allow for a actor or a red team to do is to create different profiles for how the c2s are carried out which means that you can use these to bypass AV by creating your own form of C2 Communications along with changing how the binary operates and all of this put together will make for i