

Not all formats, including xhtml, are developed to be easily edited. Even though a lot of tools can help us modify all form formats, no one has yet invented an actual all-size-fits-all solution.
DocHub offers a easy and streamlined solution for editing, handling, and storing documents in the most widely used formats. You don't have to be a tech-knowledgeable person to strike out inscription in xhtml or make other modifications. DocHub is robust enough to make the process easy for everyone.
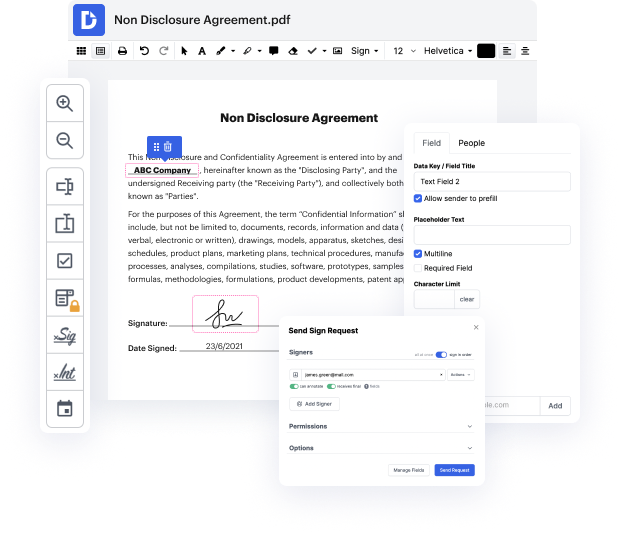
Our tool allows you to alter and tweak documents, send data back and forth, generate dynamic documents for data collection, encrypt and shield documents, and set up eSignature workflows. Moreover, you can also generate templates from documents you utilize on a regular basis.
You’ll find a great deal of additional tools inside DocHub, such as integrations that allow you to link your xhtml form to a variety business programs.
DocHub is an intuitive, cost-effective way to handle documents and improve workflows. It offers a wide selection of features, from creation to editing, eSignature solutions, and web form creating. The program can export your paperwork in many formats while maintaining maximum protection and adhering to the highest data safety requirements.
Give DocHub a go and see just how easy your editing operation can be.
letamp;#39;s say that youamp;#39;ve encrypted some data and youamp;#39;ve put it into an email and youamp;#39;re sending me this encrypted message how do we know if that data that youamp;#39;re sending to me was really secure all the way between you and me and that nobody in the middle was able to gain access to that information this is the challenge we have when dealing with cryptographic attacks the attacker often doesnamp;#39;t have the key to be able to decrypt whatamp;#39;s there so instead they use other techniques to try to gain access to the data very often even though they donamp;#39;t have the combination of the safe they may be able to break in through other parts of the safe to gain access to whatamp;#39;s inside attackers spend a lot of time trying to find inconsistencies problems and cryptographic vulnerabilities with these methods that we use to transfer data from point a to point b and very often itamp;#39;s not the cryptography thatamp;#39;s the problem ita