

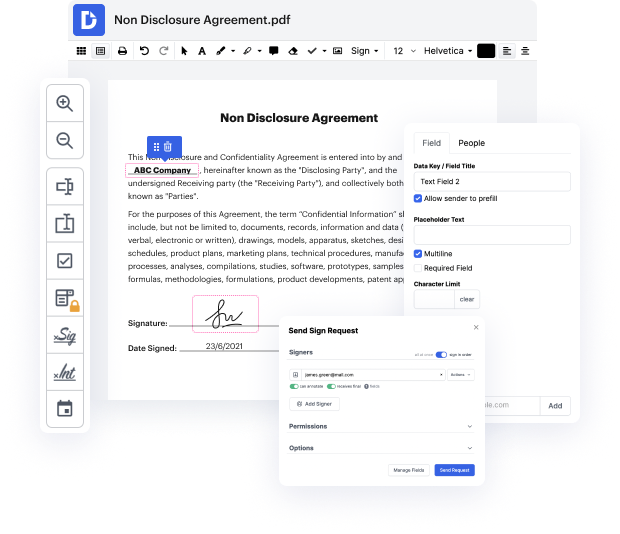
No matter how labor-intensive and challenging to modify your documents are, DocHub gives an easy way to change them. You can change any part in your CCF with no extra resources. Whether you need to tweak a single component or the entire form, you can entrust this task to our powerful tool for fast and quality results.
In addition, it makes certain that the final file is always ready to use so that you can get on with your tasks without any slowdowns. Our all-purpose set of tools also comes with pro productivity features and a library of templates, allowing you to take full advantage of your workflows without the need of wasting time on routine tasks. In addition, you can gain access to your papers from any device and integrate DocHub with other apps.
DocHub can handle any of your form management tasks. With an abundance of tools, you can create and export paperwork however you prefer. Everything you export to DocHub’s editor will be stored safely for as long as you need, with strict protection and information protection frameworks in place.
Try out DocHub today and make handling your documents more seamless!
hi welcome back to another episode on how to hack and today weamp;#39;ll be learning about cross site request for audrey so what exactly is cross-site request for audrey no worries i know there are a lot of technical terms in the area of adequate hacking and penetration testing but all you got to do is just break down what is going on when it comes to the terms so over here as you can see iamp;#39;m actually on web code so web goat is a vulnerable web application system for us to learn about ethical hacking and penetration testing on web application platforms so right here we have cross site request for authority so the whole idea of it is that the hackers will actually craft their own forms and then after which they will send it over to an authenticated user who is trying to go into a site so thatamp;#39;s the whole idea of cross site meaning that the form is actually hosted on a completely different site and the hacker could change the content of it and then send it over t