


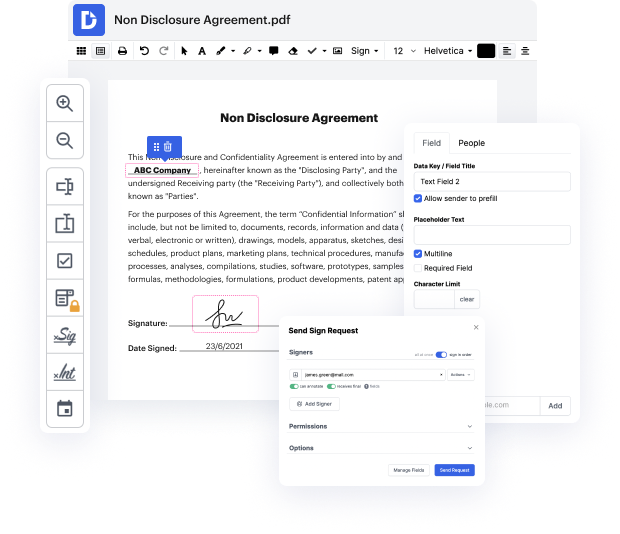
No matter how complex and difficult to edit your files are, DocHub delivers a simple way to change them. You can modify any part in your Sxw without effort. Whether you need to modify a single component or the entire document, you can rely on our robust solution for quick and quality results.
In addition, it makes certain that the final file is always ready to use so that you’ll be able to get on with your tasks without any slowdowns. Our all-purpose group of tools also comes with sophisticated productivity features and a catalog of templates, allowing you to make best use of your workflows without the need of losing time on recurring activities. Moreover, you can gain access to your papers from any device and incorporate DocHub with other apps.
DocHub can take care of any of your document management activities. With a great deal of tools, you can generate and export papers however you prefer. Everything you export to DocHub’s editor will be saved securely for as long as you need, with strict protection and information security protocols in place.
Try out DocHub today and make handling your documents easier!
a honeypot is a system or series of systems thatamp;#39;s designed to look very attractive to an attacker and hopefully the attacker will try to gain access to these honeypot systems that are on your network the actual attacker is probably not a human being itamp;#39;s probably an automated system but that means that we can look to see what processes the attackers are using to identify and then what methods theyamp;#39;re using during their attack of these types of systems the honeypot is effectively a virtual world so that the attacker would be trying to gain access to a system and not to your actual production data thereamp;#39;s many different kinds of honeypot software that you could on your network you could use kippo google hack honeypot or wordpot for example and with the software youamp;#39;d it is a constant battle to make sure that the software youamp;#39;re using is something that can accurately represent real data and real systems the attackers have systems in place t