

Flaws exist in every solution for editing every file type, and despite the fact that you can use many solutions on the market, not all of them will suit your specific requirements. DocHub makes it much simpler than ever to make and change, and manage documents - and not just in PDF format.
Every time you need to swiftly paste authentication in ACL, DocHub has got you covered. You can easily modify form elements including text and images, and layout. Personalize, organize, and encrypt documents, build eSignature workflows, make fillable forms for stress-free information gathering, etc. Our templates option enables you to generate templates based on documents with which you frequently work.
Moreover, you can stay connected to your go-to productivity capabilities and CRM platforms while handling your documents.
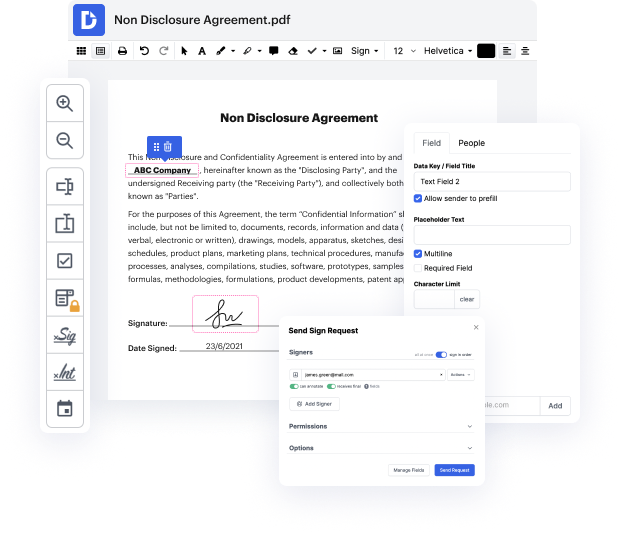
One of the most extraordinary things about using DocHub is the ability to manage form tasks of any difficulty, regardless of whether you require a fast tweak or more complex editing. It includes an all-in-one form editor, website form builder, and workflow-centered capabilities. Moreover, you can be certain that your documents will be legally binding and adhere to all protection protocols.
Cut some time off your projects with the help of DocHub's features that make managing documents effortless.
There are a few ways that we can control access to our buckets and the objects that we store within our S3 buckets, so in this lesson, Iamp;#39;m going to walk you through IAM policies, bucket policies, and access control lists. And then in the next couple of lessons, weamp;#39;ll do hands-on to see these in action as well. So firstly, we have policies created in the Identity and Access Management service. Now, these are identity-based policies, which means that they get associated with principles like users and roles. So with an IAM policy, weamp;#39;re directly applying the permissions that we want to assign to a principal, to that principal. Or we might be applying them to a group by attaching a policy to a group and then adding a user into the group. We can specify what actions are allowed on what AWS resources. So we can say that youamp;#39;re allowed to perform specific actions on a specific bucket, for example. So with IAM policies, these are atta