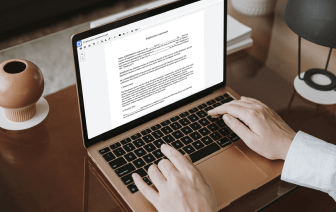
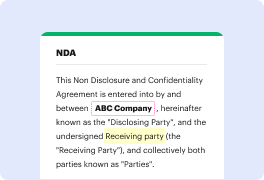


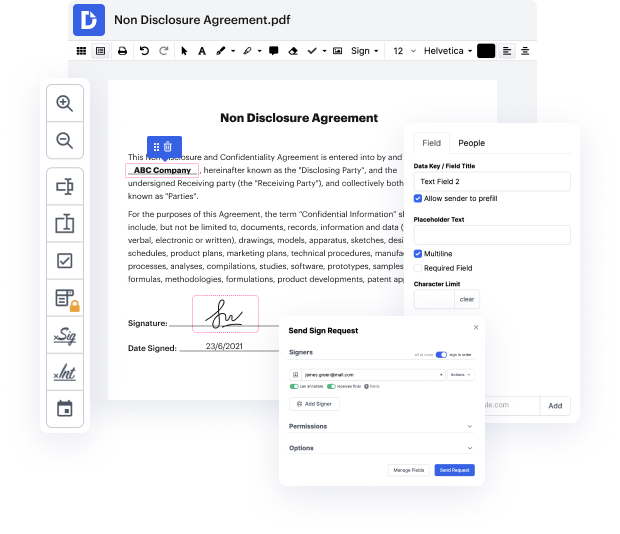
You no longer have to worry about how to inlay attribute in DOCM. Our powerful solution guarantees simple and quick document management, allowing you to work on DOCM documents in a couple of moments instead of hours or days. Our platform includes all the features you need: merging, adding fillable fields, signing forms legally, placing signs, and so on. There’s no need to install additional software or bother with pricey applications requiring a powerful device. With only two clicks in your browser, you can access everything you need.
Start now and handle all various types of forms professionally!
one thing to highlight here is the importance of the advanced security information model or asim which is the guiding framework to which normalization happens within microsoft sentinel letamp;#39;s take an example of a hypothetical proprietary network solution and see how we can leverage asim to easily apply existing detections on this custom data source here iamp;#39;m ingesting a custom network log that provides two main fields one event info and another being the event message now looking into the message field there is some consistency in the way the entries are being written and what we can do here is to use the parse function which allows us to essentially build a key value pair and match the structure of the entry into the different components we would like to extract so herein youamp;#39;ll notice weamp;#39;re extracting network protocol which would be tcp or udp we have and will exclude the request from text and continue to pull out things like source ip address port numbe