

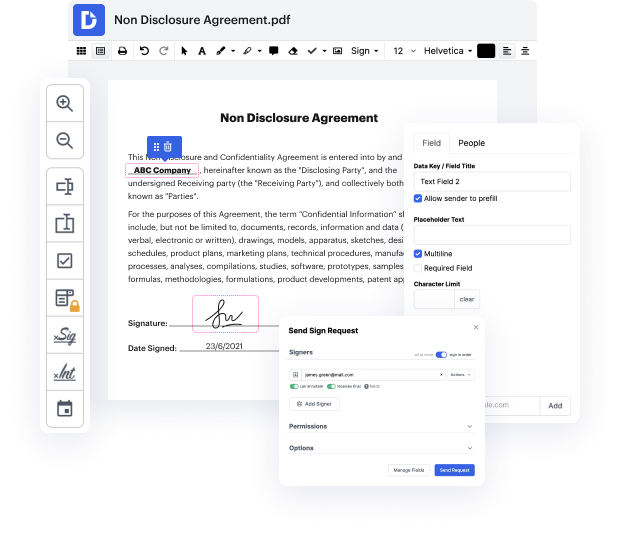
EGT may not always be the easiest with which to work. Even though many editing features are out there, not all provide a easy solution. We designed DocHub to make editing straightforward, no matter the document format. With DocHub, you can quickly and effortlessly inject type in EGT. In addition to that, DocHub provides a range of other features such as form generation, automation and management, sector-compliant eSignature solutions, and integrations.
DocHub also allows you to save effort by creating form templates from documents that you use regularly. In addition to that, you can take advantage of our numerous integrations that enable you to connect our editor to your most utilized applications effortlessly. Such a solution makes it quick and easy to deal with your files without any slowdowns.
DocHub is a helpful tool for personal and corporate use. Not only does it provide a all-encompassing suite of tools for form creation and editing, and eSignature integration, but it also has a range of features that prove useful for producing complex and straightforward workflows. Anything added to our editor is stored safe according to leading field requirements that safeguard users' data.
Make DocHub your go-to choice and streamline your form-driven workflows effortlessly!
A code injection attack is when the attacker puts their own code into an existing data stream. This is often enabled because of bad programming with an application. An application shouldnamp;#39;t allow you to put your own code into a data stream. But, often, the code is not checked by the application, and attackers are able to exploit that vulnerability. Thereamp;#39;s many different types of code that you can inject. You can inject HTML, or LDAP, or SQL code-- and any one of those may be able to manipulate or gather information from a machine, especially if you have control over the type of code that you would put into that data stream. One very common code injection type is a SQL injection. SQL stands for Structured Query Language-- or SQL. This is a very common relational database used on many websites. If you can circumvent the web front end, then you can gain access to the data thatamp;#39;s in that database. Of course, the web front end should not allow these types of request