

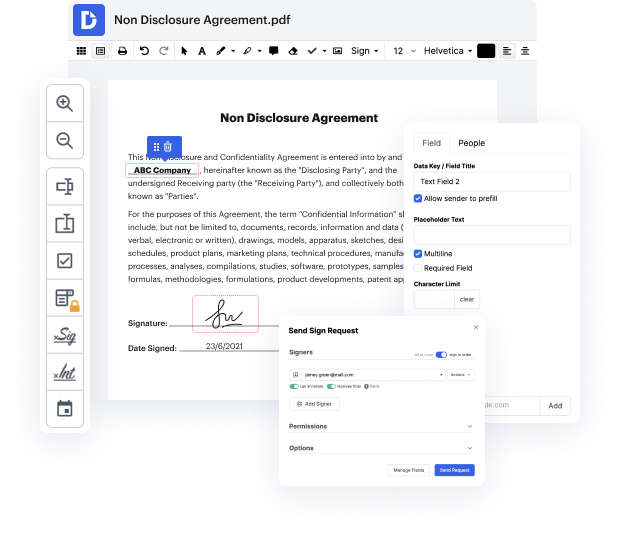
html may not always be the easiest with which to work. Even though many editing capabilities are available on the market, not all provide a straightforward tool. We developed DocHub to make editing effortless, no matter the document format. With DocHub, you can quickly and easily inject social security number in html. In addition to that, DocHub delivers a variety of other features including document generation, automation and management, field-compliant eSignature tools, and integrations.
DocHub also lets you save effort by creating document templates from documents that you use frequently. In addition to that, you can take advantage of our a wide range of integrations that enable you to connect our editor to your most used applications with ease. Such a tool makes it quick and easy to work with your documents without any delays.
DocHub is a useful tool for individual and corporate use. Not only does it provide a comprehensive suite of features for document generation and editing, and eSignature implementation, but it also has a variety of capabilities that come in handy for creating multi-level and simple workflows. Anything added to our editor is kept risk-free according to leading field requirements that shield users' data.
Make DocHub your go-to option and streamline your document-centered workflows with ease!
hey guys welcome back to the bug bounty series in this video weamp;#39;re going to be taking a look at html injection more specifically weamp;#39;re going to be taking a look at reflected hd html injection with the post request now as i mentioned weamp;#39;re going to be using a beatbox that contains b web and iamp;#39;m going to start it off you know chronologically within injection i know weamp;#39;ve taken a look at reflected injection with the get request we also took a look at iframe injection and php code injection so weamp;#39;ll be completing the rest of these various types of injections as we move along that being said letamp;#39;s get started so the first thing iamp;#39;m going to do is iamp;#39;m just going to click on the html injection reflected post using the post request so again this is a very very simple attack to understand uh in regards to the actual injection what is going to happen here is weamp;#39;re going to intercept the post request that is being sen