

It is usually difficult to get a platform that can cover all your organizational needs or provides you with appropriate tools to handle document generation and approval. Picking an application or platform that combines essential document generation tools that streamline any task you have in mind is vital. Although the most widely used file format to work with is PDF, you need a comprehensive solution to manage any available file format, including ODM.
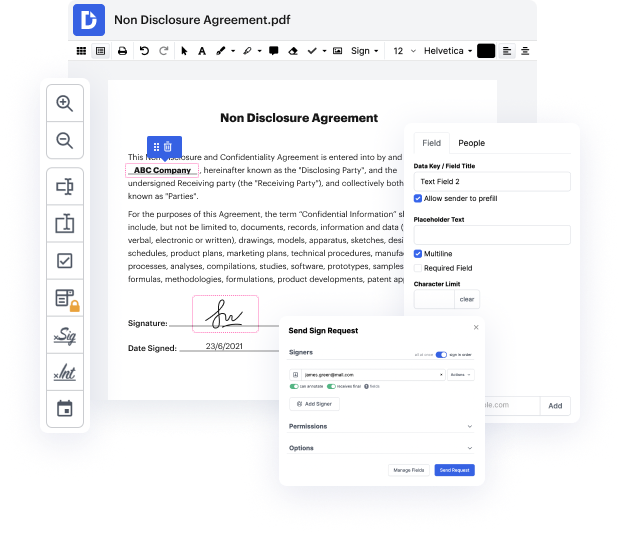
DocHub helps to ensure that all your document generation demands are taken care of. Modify, eSign, rotate and merge your pages in accordance with your preferences by a mouse click. Deal with all formats, including ODM, efficiently and fast. Regardless of the file format you begin dealing with, you can easily change it into a required file format. Save tons of time requesting or looking for the right file format.
With DocHub, you don’t require more time to get familiar with our interface and editing procedure. DocHub is surely an easy-to-use and user-friendly software for anybody, even those with no tech education. Onboard your team and departments and transform file management for the business forever. enter PII in ODM, generate fillable forms, eSign your documents, and have things carried out with DocHub.
Reap the benefits of DocHub’s substantial feature list and quickly work with any file in any file format, such as ODM. Save your time cobbling together third-party solutions and stick to an all-in-one software to boost your day-to-day operations. Start your cost-free DocHub trial today.
[Music] personally identifiable information what is pii pii is personally identifiable information that includes a persons name the names of family or friends addresses dates and places of birth social security numbers account numbers and even employee id numbers a personal data bdocHub occurs when pii is released to an unauthorized actor through email phishing attacks ransomware and even exploiting a victims digital footprints a digital footprint could be a potential piece of pii that exists on the internet as a result of a persons online activity easily harvested and then exploited by a threat actor cyber criminals can post ads on the dark web selling ones pii the identities are then bought by thieves to take part in tax fraud open fake accounts to apply for credit cards apply for work apply for a place to live and other exploitative crimes attackers can gather pii from anywhere including public forums and social media every type of organization businesses clinics and even school