

People often need to blot authentication in xht when processing forms. Unfortunately, few applications offer the tools you need to accomplish this task. To do something like this normally involves changing between multiple software applications, which take time and effort. Luckily, there is a solution that works for almost any job: DocHub.
DocHub is an appropriately-built PDF editor with a complete set of helpful functions in one place. Editing, signing, and sharing documents is easy with our online tool, which you can use from any online device.
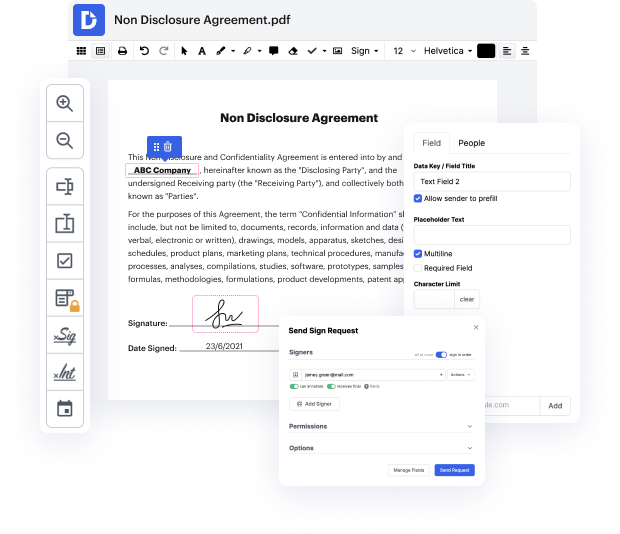
By following these five easy steps, you'll have your revised xht rapidly. The user-friendly interface makes the process fast and productive - stopping jumping between windows. Try DocHub now!
todayamp;#39;s sports wiger tutorial is entitled Json web authentication bypass via jku header injection this lab uses a Json web based mechanism for handling sessions because of this we are going to be using BPamp;#39;s JWT editor extension so make sure you have it installed this lab server supports the Json web key set URL or jku parameter in the Json web header a Json web key set is a Json object containing an array of Json web keys representing different keys this means that instead of embedding public Keys directly into the Json web jwk header parameter like we did in the previous lab we are going to be using the jku header parameter to reference an URL when verifying the signature the server fetches the key from the provided URL secure websites will only fetch keys from trusted domains however this lab server fails to check whether the provided URL belongs to a trusted domain before fetching the key to solve the lab we must access the admin panel located at/ admin and delete th