

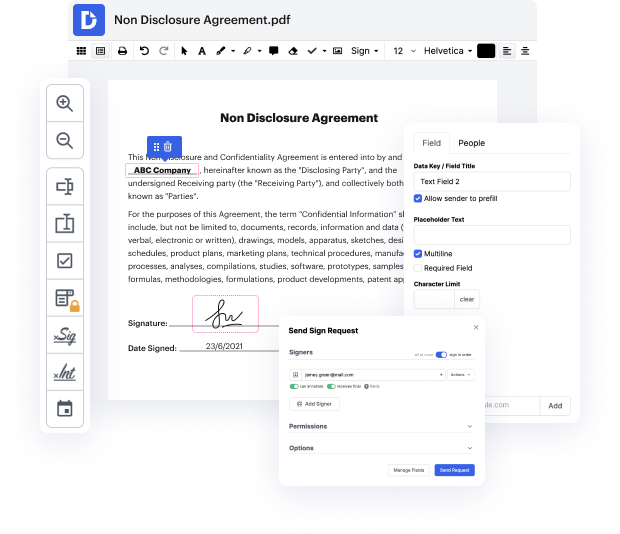
DocHub is an all-in-one PDF editor that allows you to blot authentication in HWPML, and much more. You can underline, blackout, or remove paperwork elements, add text and images where you need them, and collect data and signatures. And since it runs on any web browser, you won’t need to update your hardware to access its robust features, saving you money. When you have DocHub, a web browser is all it takes to make changes in your HWPML.
Log in to our website and adhere to these steps:
It couldn't be simpler! Enhance your document management now with DocHub!
Todayamp;#39;s PortSwigger tutorial is entitled: JWT authentication bypass via flawed signature verification. To solve the lab, we must access the admin panel and delete the user amp;quot;Carlosamp;quot;. As with the previous lab, we are going to be using Burpamp;#39;s amp;quot;JWT Editoramp;quot; extension. This way, it is easier to read and modify the contents of the JWT. If you do not have the extension installed, go to Burp -amp;gt; Extensions -amp;gt; BApp Store and search for amp;quot;JWT Editoramp;quot;. Select the extension and click amp;quot;amp;quot; to it. Now, access the lab and log in with the provided credentials: wiener peter. Letamp;#39;s also try accessing the admin panel. We know from the labamp;#39;s description that the admin panel is located at amp;quot;/adminamp;quot;. If we did not have this information, we could have used Burpamp;#39;s amp;quot;content discoveryamp;quot; functionality to automatically discover hidden content on the website, as